As we work for our customers, we often find ourselves in a position where we know it's not only our problem but most likely, a lot of people will hit this sooner or later. This Technical Hub provides our customers and us with solutions, scripts, and other information useful for Administrators and, to some degree, for non-technical people.
Sending emails in Microsoft Exchange world using an alias for an account has always been a pain. It required working with workarounds such as setting up Shared Mailbox or Distribution Groups and using SendAs permissions. For years admins around the world were asking Microsoft to change this, and finally, in April 2021, they did! It's a new feature of Office 365, and it requires action from Office 365 Administrator.
Since my website went down in fire with OVH SBG2, I used this occasion to publish my restored website via Cloudflare. It allows me to have to cache, minimization, and some additional security. One thing that caught my attention while browsing through Cloudflare settings was the Always Online feature based on web.archive.org. Basically, the concept is – whenever the website is down, Cloudflare would go and fetch content from web.archive.org.
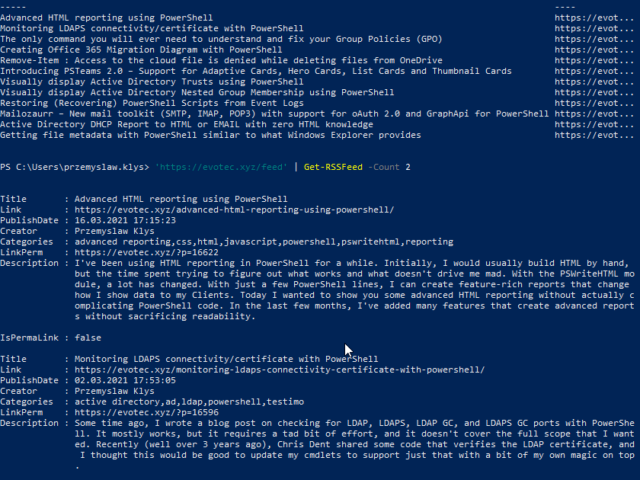
I've been using HTML reporting in PowerShell for a while. Initially, I would usually build HTML by hand, but the time spent trying to figure out what works and what doesn't drive me mad. With the PSWriteHTML module, a lot has changed. With just a few PowerShell lines, I can create feature-rich reports that change how I show data to my Clients. Today I wanted to show you some advanced HTML reporting without actually complicating PowerShell code. In the last few months, I've added many features that create advanced reports without sacrificing readability.
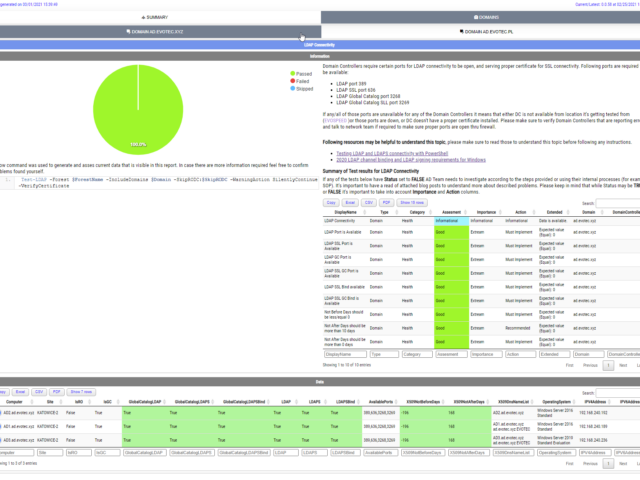
Some time ago, I wrote a blog post on checking for LDAP, LDAPS, LDAP GC, and LDAPS GC ports with PowerShell. It mostly works, but it requires a tad bit of effort, and it doesn't cover the full scope that I wanted. Recently (well over 3 years ago), Chris Dent shared some code that verifies the LDAP certificate, and I thought this would be good to update my cmdlets to support just that with a bit of my own magic on top.
I've been working on cleaning up Group Policies for a couple of months. While it may seem trivial, things get complicated when you're tasked with managing 5000 GPOs created over 15 years by multiple teams without any best practices in mind. While working on GPOZaurr (my new PowerShell module), I've noticed that the more code I wrote to manage those GPOs, the more I knew passing this knowledge to admins who will be executing this on a weekly/monthly basis is going to be a challenge. That's why I've decided to follow a similar approach as my other Active Directory testing module called Testimo. I've created a single command that analyses Group Policies using different methods and shows views from different angles to deliver the full picture. On top of that, it provides a solution (or it tries to) so that it's fairly easy to fix – as long as you agree with what it proposes.
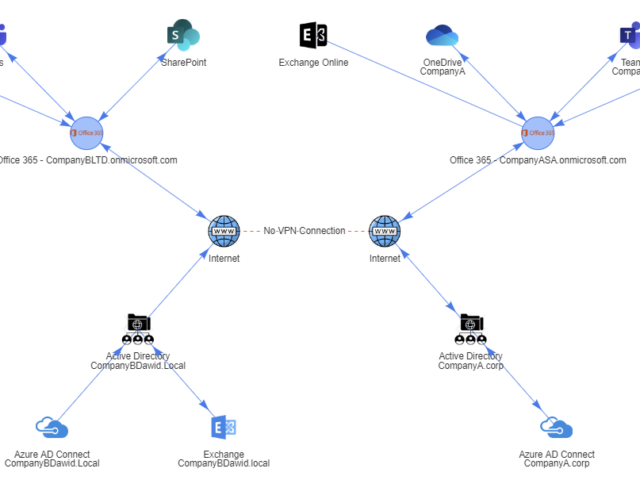
A few weeks ago, I posted a concept migration diagram for Office 365 to Twitter and Facebook. Today I thought I would show you how you can do it yourself using PowerShell and PSWriteHTML PowerShell module. When I started working on this, I've thought I want to create before and after infrastructure to see how it will look when migration ends. I've initially planned to assign myself an Office 365 Visio Plan 2 license and do something manually, thinking it may be just much easier. Unfortunately for me, there were no free Visio licenses in my tenant, and my laziness took over, so I've decided to give it a go using PowerShell only.
I like OneDrive. It allows me to keep my data secure and always synchronized. If things go wrong, I can always get it back. I use it for almost everything. Even for my PowerShell projects, which are committed to GitHub, so in theory, I shouldn't need that. But every once in a while, I make some stupid mistake and delete a file that has yet not been committed to GitHub, and that's where the OneDrive comes in handy. Quick restore, and we're back. Unfortunately, sometimes things aren't as I would expect them to work. For example, let's have a look at this nice list of markdown files that are documentation for my module called GPOZaurr.
PSTeams PowerShell module has been on the market for a while now. It supports sending notifications to Microsoft Teams channels via Incoming WebHooks. You could send a pretty message to the team's channel with just a few lines of code. With PSTeams 2.0, support for Adaptive Cards, Hero Cards, List Cards, and Thumbnail Cards was added.
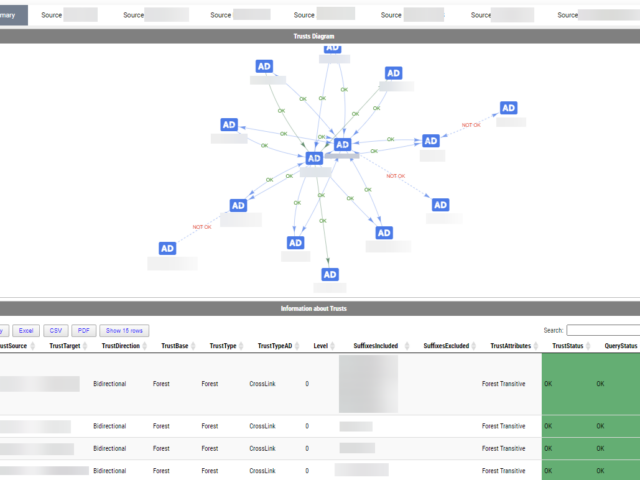
Active Directory Trusts are useful to connect one or more domains. But as useful those are, they can be very dangerous. Also, keeping trusts working and in good shape should be a top priority for Active Directory Admins. While there is a couple of command in the Active Directory module Get-ADTrust, I thought I would try and write my own that checks a few more things. I want to thank Chris Dent for his input on the part of this command. His binary skills amaze me!
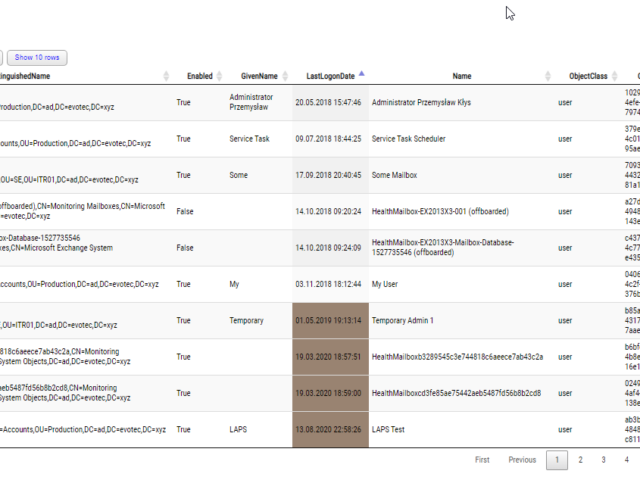
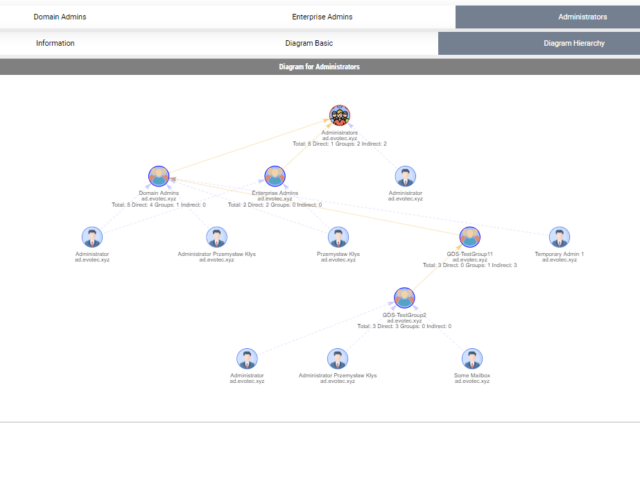
In the Active Directory PowerShell module, you have two commands to your disposal that help display group membership. Those are Get-ADGroup and Get-ADGroupMember. The first command contains property Members, which gives you DistinguishedName of all members, and Get-ADGroupMember can provide you either direct members or with Recursive switch all members recursively (skipping groups). Till a few weeks ago, I was a happy user of those commands until I noticed two things. Member property for Get-ADGroup sometimes misses elements for whatever reason.