Security Identifier (SID) History is a useful mechanism in Active Directory (AD) migrations. It allows users and groups in a new domain to retain access to resources that still rely on permissions from the old domain. However, once migrations are completed, these historical SIDs can become clutter, posing both security and administrative challenges. While it’s best to remove unnecessary SID History as soon as you’re done migrating, many environments skip this step. Over time, decommissioned or broken trusts make cleanup more difficult, and domain objects can accrue so many old entries that you lose track of what is still required.
Active Directory
Have you ever looked at your Active Directory and wondered, “Why do I still have computers listed that haven’t been turned on since World Cup 2016?” Yeah, we’ve all been there. Keeping AD clean and up-to-date is like trying to organize your garage—it’s easy to put off until it becomes a total mess.
Active Directory replication is a critical process that ensures the consistent and up-to-date state of directory information across all domain controllers in a domain. Monitoring this process is important as it helps identify any issues that may arise and resolve them quickly. One way to monitor Active Directory replication is by using the Repadmin command-line tool. Repadmin provides a wealth of information about the replication status and health of a domain. However, manually checking the Repadmin output can be time-consuming and tedious, and running it manually every 30 minutes just to check if everything is great doesn’t seem like a great idea. While PowerShell has its own commands around replication I’ve not found something as fast and reliable as repadmin /replsummary.
Active Directory (AD) is crucial in managing identities and resources within an organization. Ensuring its health is pivotal for the seamless operation of various services. Today, I decided to look at Microsoft Entra Connect Health (Azure AD Connect Health) service, which allows monitoring Azure AD Connect, ADFS, and Active Directory. This means that under a single umbrella, you can have an overview of three services health. But is it worth it?
I was scrolling X (aka Twitter) today and saw this blog post, “PowerShell: Report On-Premises Active Directory Accounts that are Synchronized with Azure AD Connect” by Kevin Trent. I like reading blog posts as I tend to learn some new things and see how people tend to solve their problems.
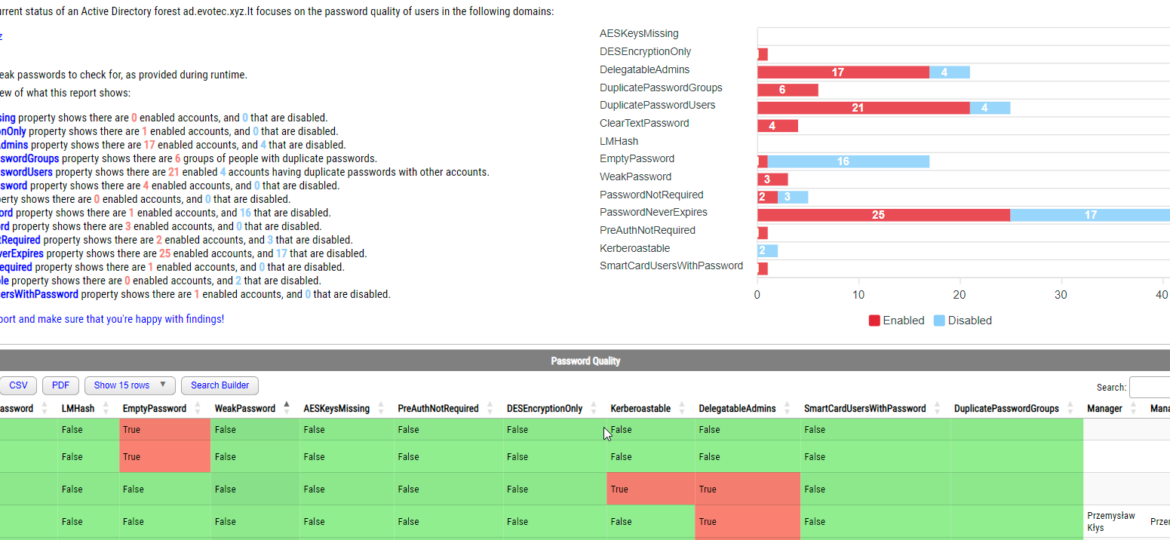
PasswordSolution uses the DSInternals PowerShell module to gather Active Directory hashes and then combines that data into a prettified report. If you have ever used DSInternals, you know that while very powerful, it comes with raw data that is hard to process and requires some skills to get it into a state that can be shown to management or security.
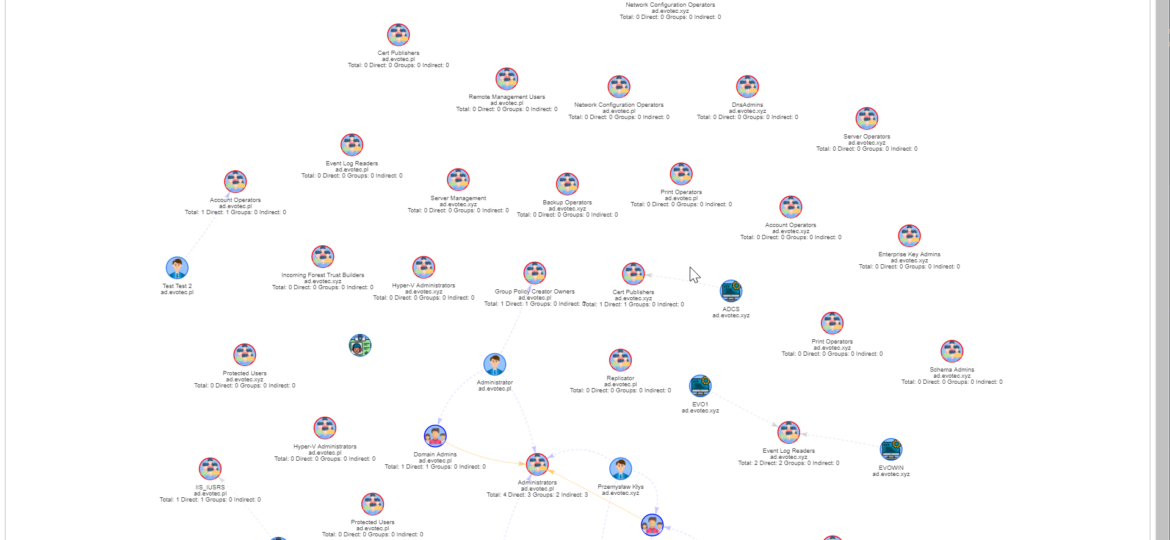
I work a lot with Active Directory-related tasks. One of the tasks is to know the group membership of critical Active Directory Groups such as Domain Admins, Enterprise Admins, Schema Admins, Event Log Readers, and a few others that are a bit less known. As I did it, I got bored of typing the group names repeatedly and decided that enough was enough and there must be an easier way for me to do that.
In my earlier blog post, I showed you a way to find duplicate DNS entries using PowerShell, but the focus was on finding duplicate entries based on hostname. But what if you would like to find duplicate entries based on IP Addresses? This was the question I was asked on Reddit, and I thought it was a legitimate request, so today’s focus will be on transposing table output from earlier functions to present data differently.
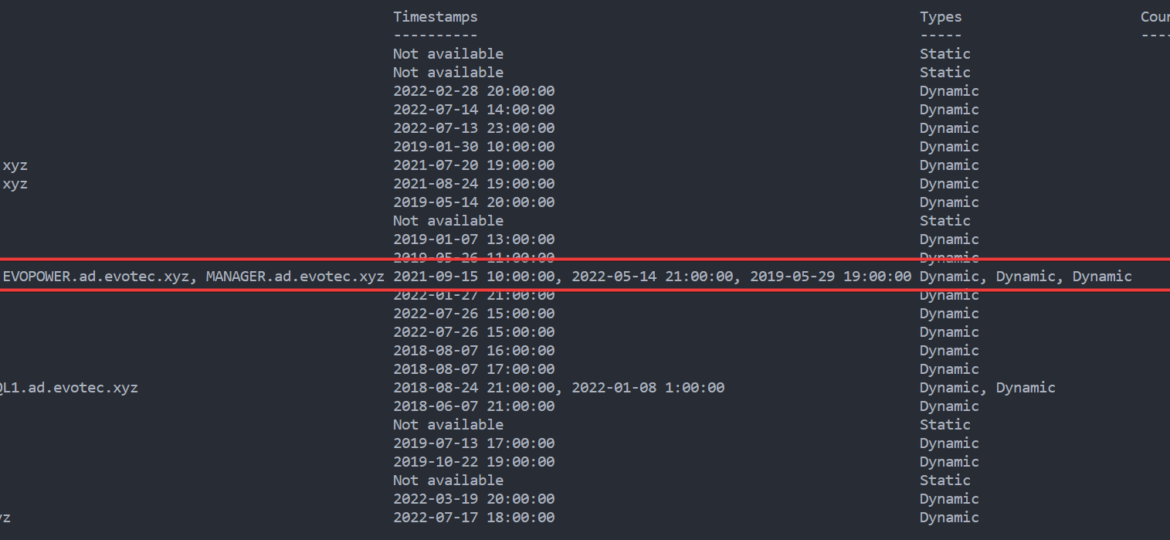
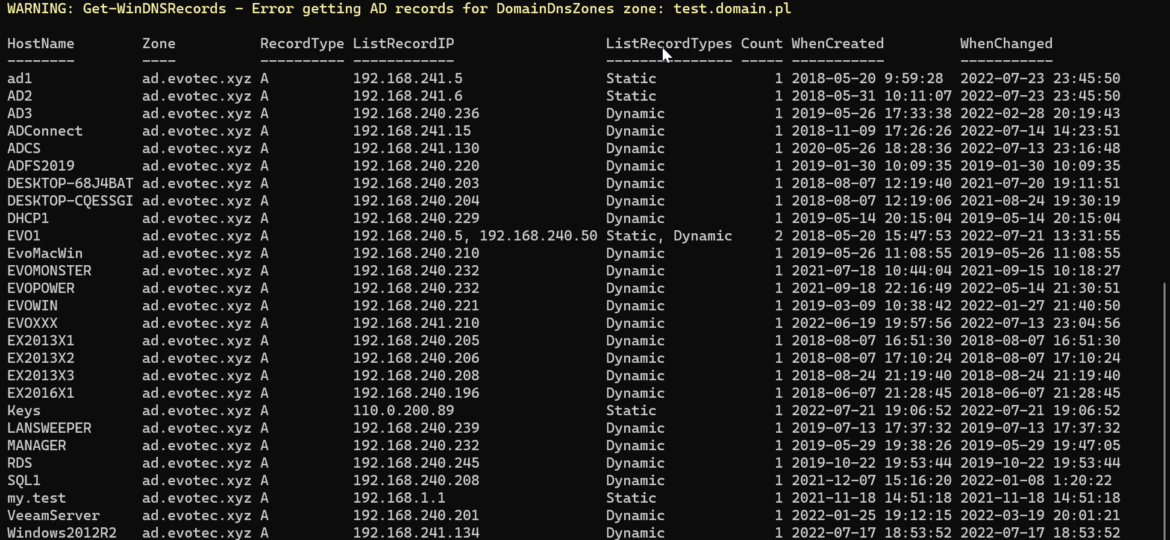
Today’s blog post is about Active Directory-integrated DNS and how to find duplicate entries. By duplicate, I mean those where one DNS name matches multiple IP addresses. While some duplicate DNS entries are expected, in other cases, it may lead to problems. For example, having a static IP assigned to a hostname that later on is also updated with dynamic entries.
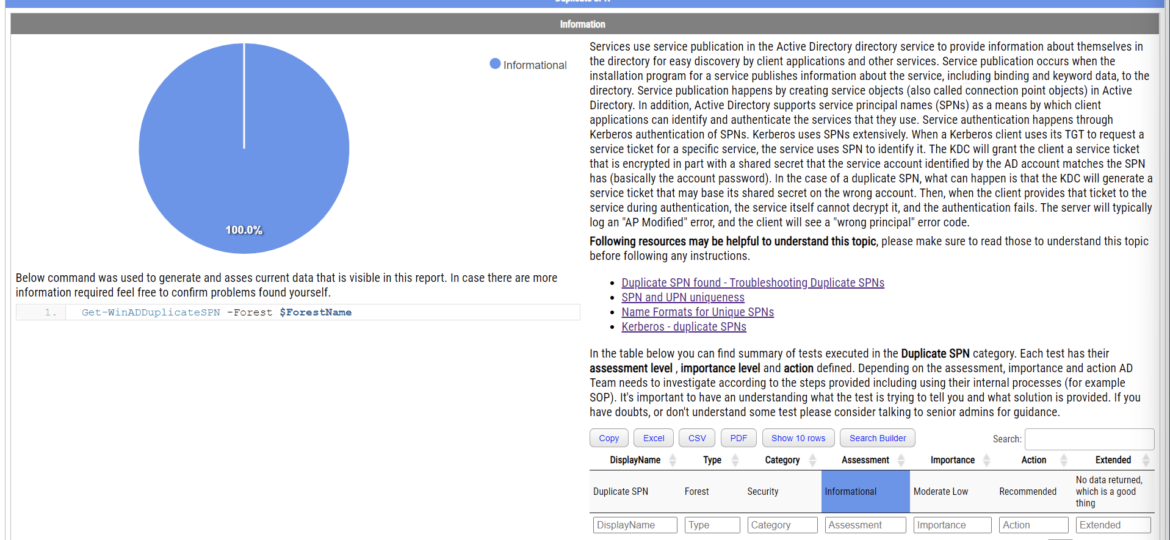
Duplicate SPNs aren’t very common but can happen in any Active Directory as there’s no built-in way that tracks and prevent duplicate SPN’s. One has to either know all SPN’s in the environment, track them or check each time whether it already exists or not. Things get more complicated with larger Active Directory environments as people change, new apps are added, old apps are forgotten, but SPNs prevail.