Today, I made the decision to upgrade my test environment and update the version of Azure AD Connect to the latest one. The process is usually simple: download a new MSI, run it, click next a few times, enter the credentials for your Global Admin, and you’re finished. However, this time, I encountered an error.
azure adconnect
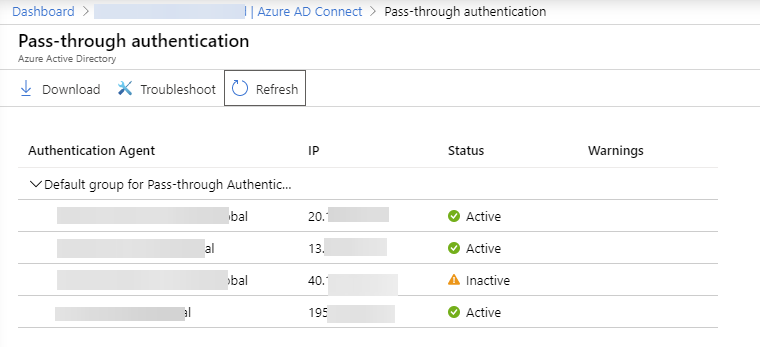
Recently I was switching Office 365 tenant from ADFS to Azure AD Pass-through authentication (PTA). It all went smoothly with one exception. After removing one of the Azure AD Connect servers and all applications from its Azure AD Connect interface still is showing said agent, just inactive.
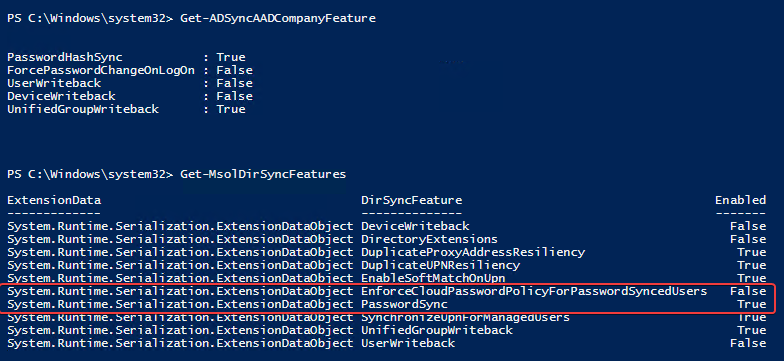
Azure AD Connect allows three ways to make sure the user password is the same in Active Directory and Office 365. Those are Password Hash Sync, Pass-Thru Authentication, and ADFS. While my preferred option to go with would be Pass-Thru Authentication, only Password Hash Synchronization is the easiest and least resource-intensive. It synchronizes user password to Office 365, and even if your Active Directory is down, you can still log in to Office 365. It’s perfect for small and even more significant companies that don’t have resources or can’t guarantee that their infrastructure will stay 100% time online so users can authenticate based on their Active Directory.