Azure AD Connect allows three ways to make sure the user password is the same in Active Directory and Office 365. Those are Password Hash Sync, Pass-Thru Authentication, and ADFS. While my preferred option to go with would be Pass-Thru Authentication, only Password Hash Synchronization is the easiest and least resource-intensive. It synchronizes user password to Office 365, and even if your Active Directory is down, you can still log in to Office 365. It's perfect for small and even more significant companies that don't have resources or can't guarantee that their infrastructure will stay 100% time online so users can authenticate based on their Active Directory.
💡 Password Hash Synchronization – Why it's a problem?
While password hash synchronization works great, it had one huge drawback. It sets the password to never expire in Office 365 regardless of what you've set up in your Active Directory. While it may not be a massive problem for some companies, it's not the same for all of them. Recent Microsoft recommendations are saying that you should set your Passwords to Never Expire, use complicated passwords and MFA (Multi-Factor Authentication). However, just because Microsoft says so doesn't mean internal rules and country laws do not require differently. If that wasn't enough, there's also another issue. If your password expires in Active Directory, it doesn't expire in Office 365. This means that while your user can't log in to Active Directory resources, he/she can still use Office 365.
💡 Password Hash Synchronization – How to make passwords expire?
Please keep in mind features described here, while working are in Public Preview. It's unlikely Microsoft will remove it, but keep this in mind.[/
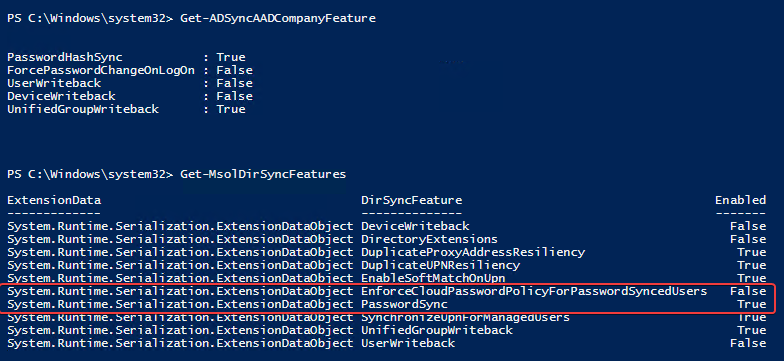
Till some time ago, there was no hope for a change, but it seems Microsoft has enhanced Password Hash Synchronization functionality. It's not readily available, and you can't just press a button in Azure AD Connect and have it enabled. You can use PowerShell to do so instead. As you can see below, there's a new option called EnforceCloudPasswordPolicyForPasswordSyncedUsers. By default, it's disabled.
Knowing this feature exists we can enable it.
Set-MsolDirSyncFeature -Feature EnforceCloudPasswordPolicyForPasswordSyncedUsers -Enable $true
Now that we've enabled password policy for password synchronized users we can verify per user settings
Get-AzureADUser | Select-Object DirSyncEnabled, PasswordPolicies, AccountEnabled
As you see, by default, the PasswordPolicy for synchronized users is still DisablePasswordExpiration. In our case we need to set it to None.
Get-AzureADUser -All $true | Where-Object { $_.DirSyncEnabled -eq $true -and $_.PasswordPolicies -eq 'DisablePasswordExpiration' } | ForEach-Object {
Set-AzureADUser -ObjectId $_.ObjectID -PasswordPolicies None
}
Keep in mind that in some cases having PasswordNeverExpire may be required (service accounts or similar). Make sure that you modify the code above to accommodate that for your environment.
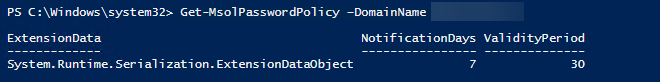
Just in case you want to verify what is the password policy applied to your users, following PowerShell command will show you the required details
Get-MsolPasswordPolicy –DomainName evotec.pl