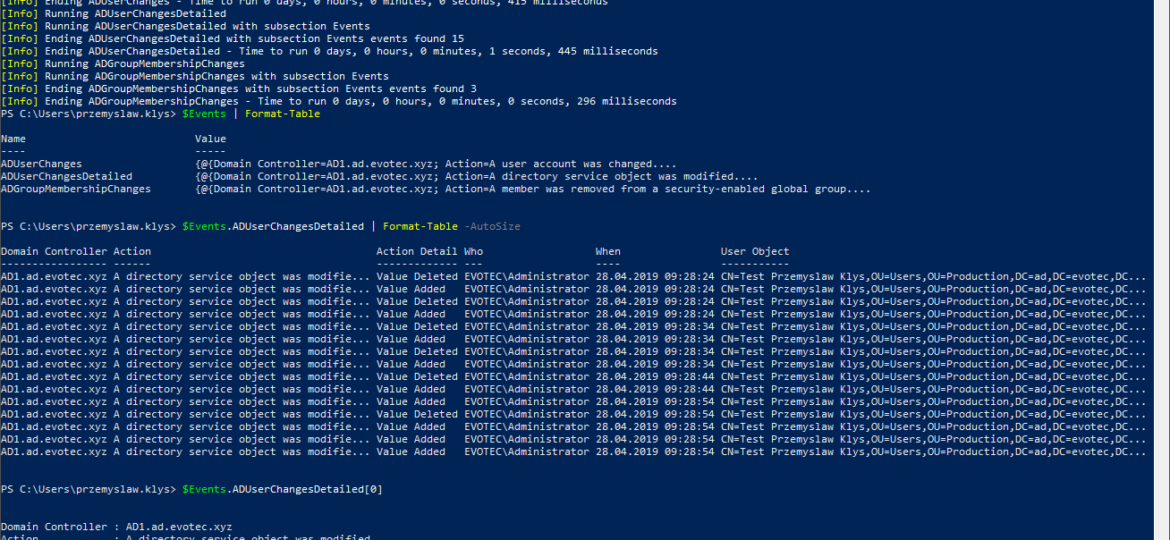
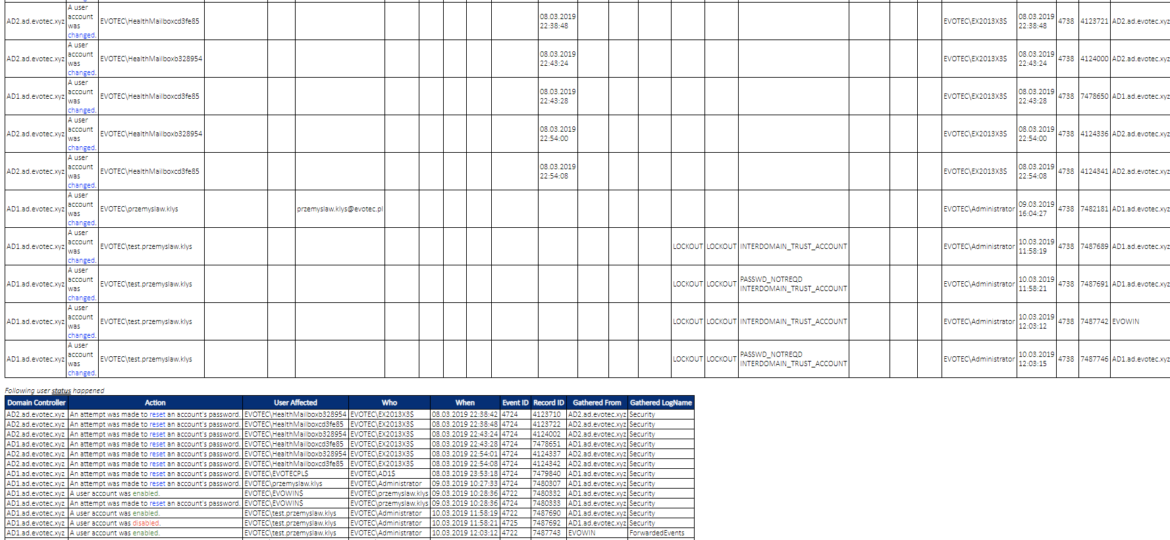
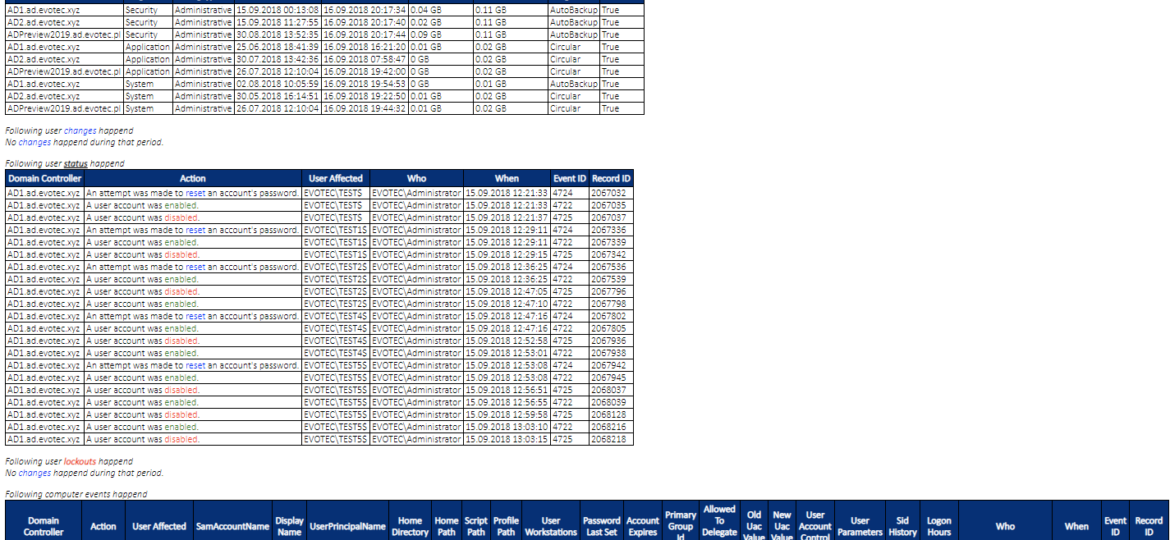
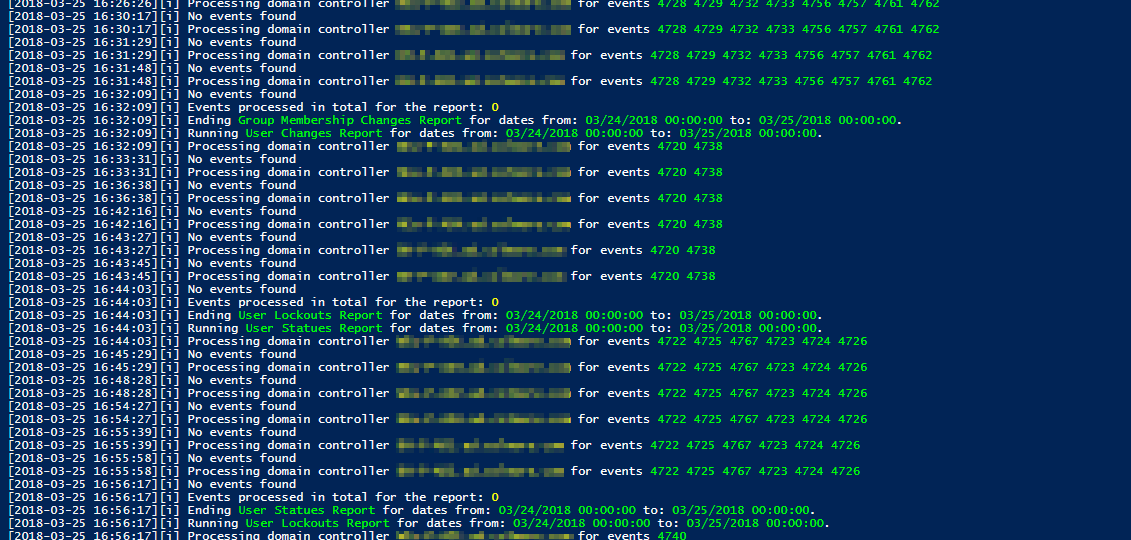
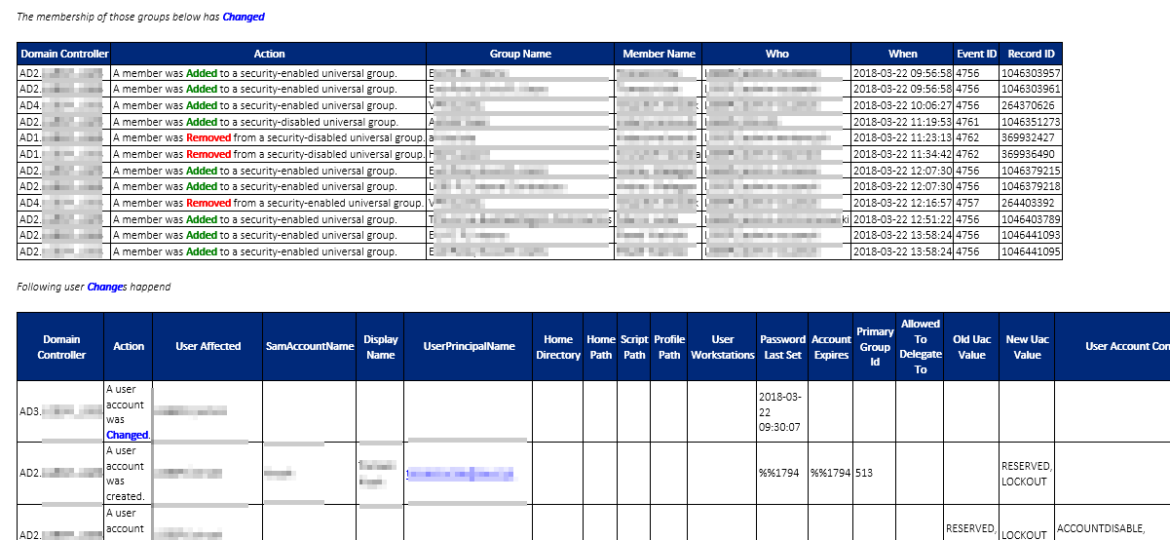
While the title of this blog may be a bit exaggeration, the command I’m trying to show here does it’s best to deliver on the promise. What you’re about to witness here is something I’ve worked on for a while now, and it meets my basic needs. If you don’t have SIEM product or products that monitor who does what in Active Directory this command makes it very easy, even for people who don’t have much experience in reading Event Logs. If you’d like to learn about working with Windows Event Logs here’s a great article I wrote recently – PowerShell – Everything you wanted to know about Event Logs and then some.
events
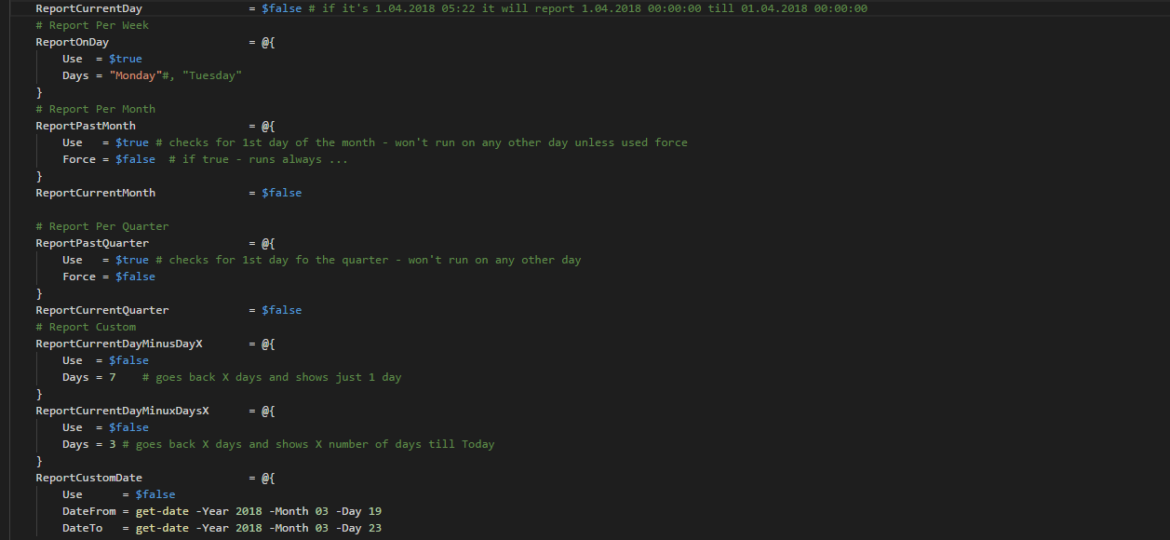
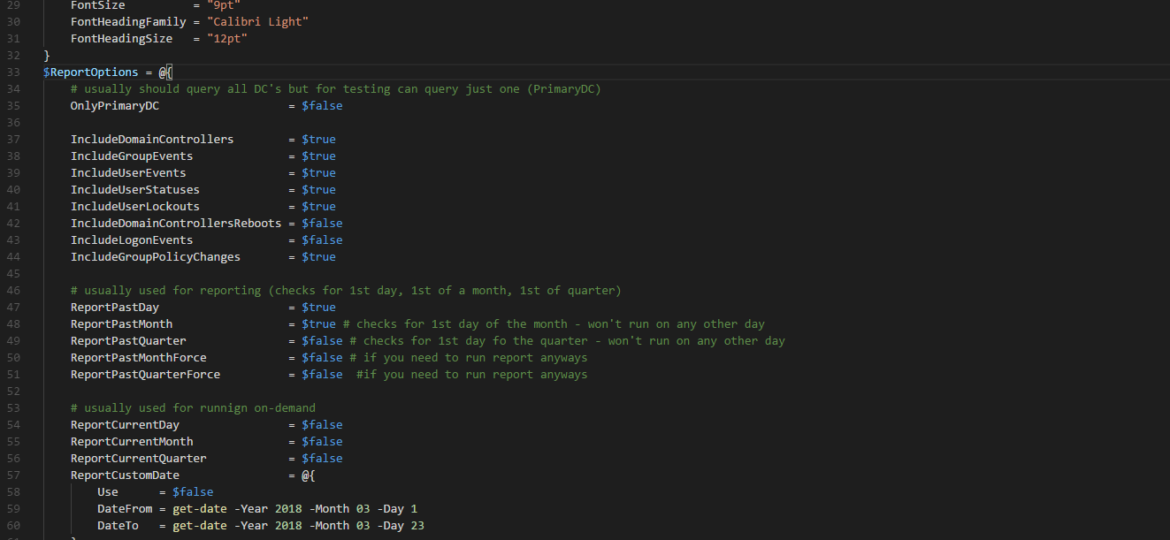
A new branch of PSWinReporting is slowly coming, and I thought it would be the best time to have a final article about it with all configuration options available for those that will want to stay using PSWinReporting from Legacy branch. The idea is that you may have it working in your systems and it’s good enough for you. You may not want to change it, and with New Hope, the changes are so big it’s a rewrite.
If you feel this title is very familiar to you it’s because I actually have stolen the title from Kevin Marquette. I’m in awe of his posts that take you thru topic from beginning till the end. No splitting, no hiding anything, everything on a plate, in a single post. That’s why I’ve decided to write a post that will take you on a trip on how to work with Event Logs, something that is an internal part of Windows Administration. If you’ve never worked with Events and you’re in IT you most likely should make an effort to find out what it is and how you can eat it.