While the title of this blog may be a bit exaggeration, the command I'm trying to show here does it's best to deliver on the promise. What you're about to witness here is something I've worked on for a while now, and it meets my basic needs. If you don't have SIEM product or products that monitor who does what in Active Directory this command makes it very easy, even for people who don't have much experience in reading Event Logs. If you'd like to learn about working with Windows Event Logs here's a great article I wrote recently – PowerShell – Everything you wanted to know about Event Logs and then some. This blog entry is based on PSWinReporting (more specifically on PSWinReportingV2) PowerShell Module – just in case you wonder.
💡 TL;DR – Too long, didn't read
What can this command do? It can deliver the following information from your Active Directory infrastructure:
- 🌐
- Computer changes – Created / Changed – ADComputerCreatedChanged
- Computer changes – Detailed – ADComputerChangesDetailed
- Computer deleted – ADComputerDeleted
- Group changes – ADGroupChanges
- Group changes – Detailed – ADGroupChangesDetailed
- Group changes – Created / Deleted – ADGroupCreateDelete
- Group enumeration – ADGroupEnumeration
- Group membership changes – ADGroupMembershipChanges
- Group policy changes – ADGroupPolicyChanges
- Logs Cleared Other – ADLogsClearedOther
- Logs Cleared Security – ADLogsClearedSecurity
- User changes – ADUserChanges
- User changes detailed – ADUserChangesDetailed
- User lockouts – ADUserLockouts
- User logon – ADUserLogon
- User logon Kerberos – ADUserLogonKerberos
- User status changes – ADUserStatus
- User unlocks – ADUserUnlocked
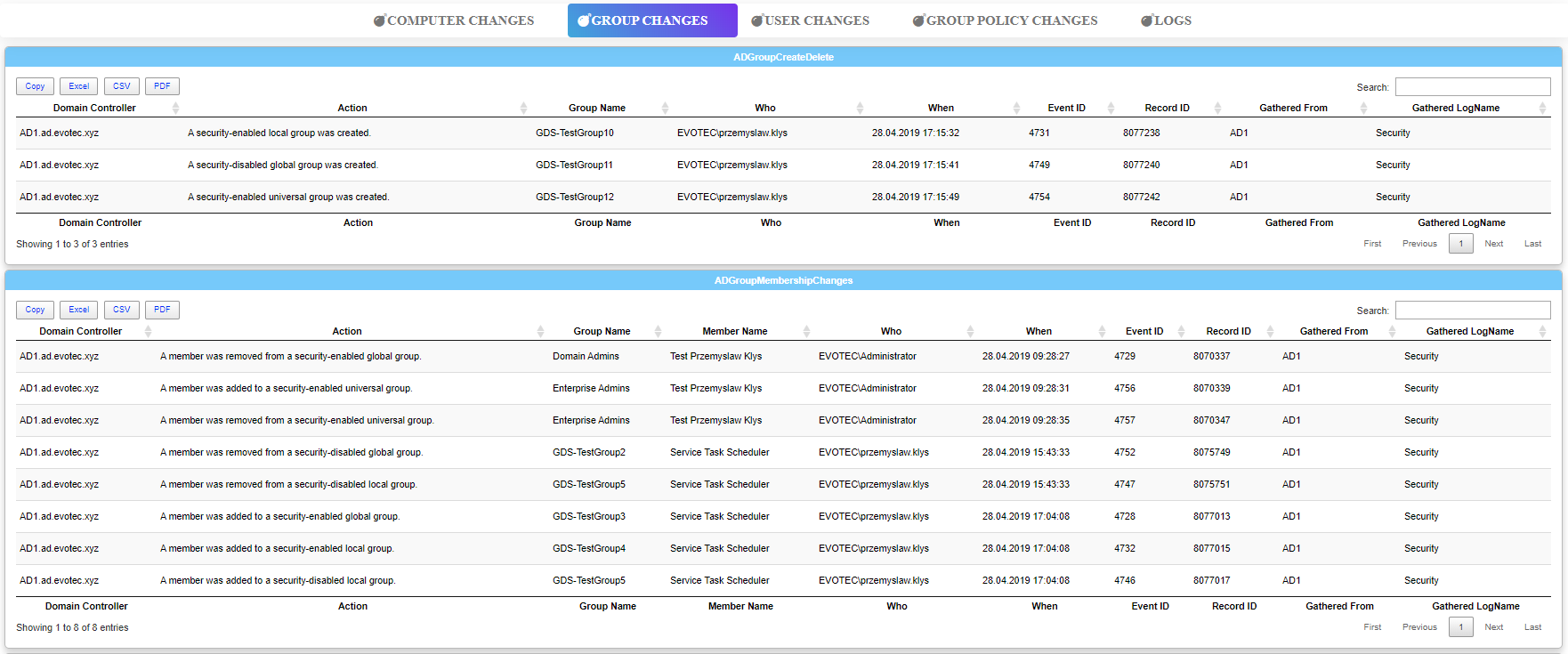
If you try to find in Google how to get each of the information shown above you would usually get a bunch of PowerShell scripts doing one thing at a time. You want to find out, where the user was locked out? Do you want to find who added a user to the Domain Admins group? All of that has already been done and described in countless articles all over the place. But what all have in common is that they require time to set up and use. Usually, it's not straight forward. You need to know EventID, EventLog name, find out on which DC action happened, and finally, each script does it in its way and only covers certain aspects of Active Directory Events. Also sometimes you're required to scan multiple Active Directory Controllers if you want your data to cover everything which is another issue you have to deal with. To lure you further into the article I've prepared a static HTML file generated in Dashimo which shows most of the data for you to view HERE.
💡 Show me what I get?
What if you could get all that in one command? What if I tell you, that the scan of all your Domain Controllers is done in parallel? You ask for data once, and it scans everything and returns you the required data. Data that is already preformatted, with proper naming in place, with all the necessary conversions. Too good to be true? I've teased that command before, but today I'm releasing it to production.
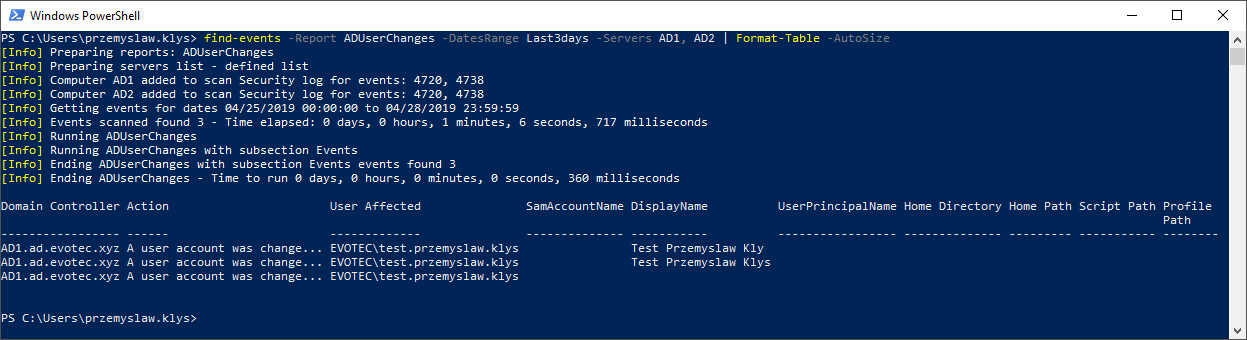
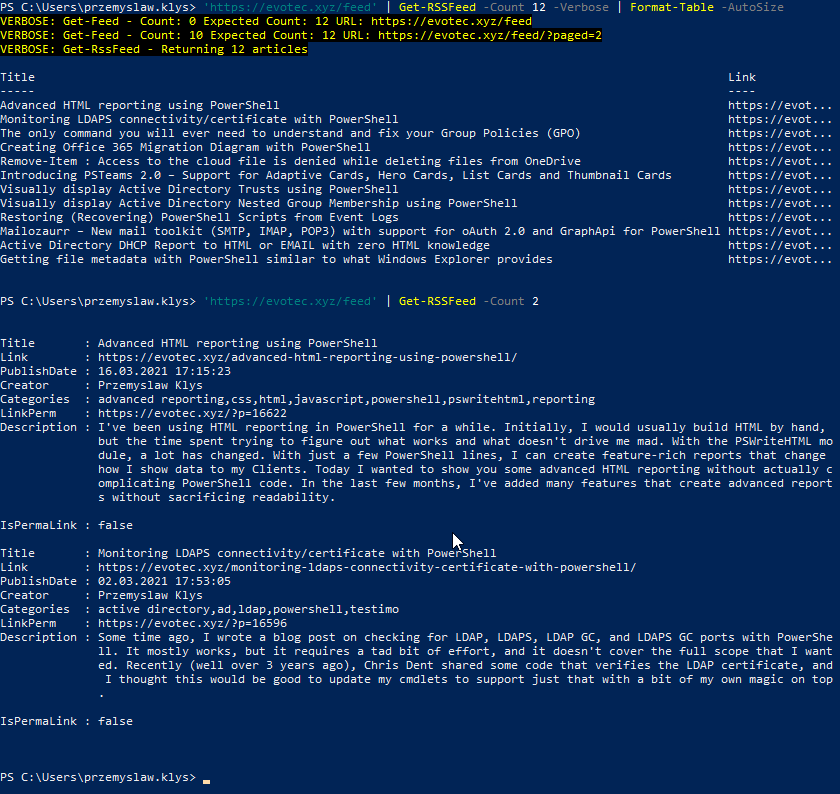
Find-Events -Report ADUserChanges -DatesRange Last3days -Servers AD1,AD2 -Quiet
So what happened there? We asked two domain controllers for AD User Changes that happened in the last 3 days. I've used quiet parameter which covered what is actually happening in the background. But if we run it without it, you will get much more information.
find-events -Report ADUserChanges -DatesRange Last3days -Servers AD1, AD2 | Format-Table -AutoSize
As you see above without Quiet parameter it gave you information that we scanned for Security Log for events 4720 and 4738 covering the last three days. We also did a scan two domain controllers, and it took 1 minute 1 and 6 seconds to deliver results. Let's now ask same Domain Controllers for Group Membership changes. Let's see who was added where and who did it.
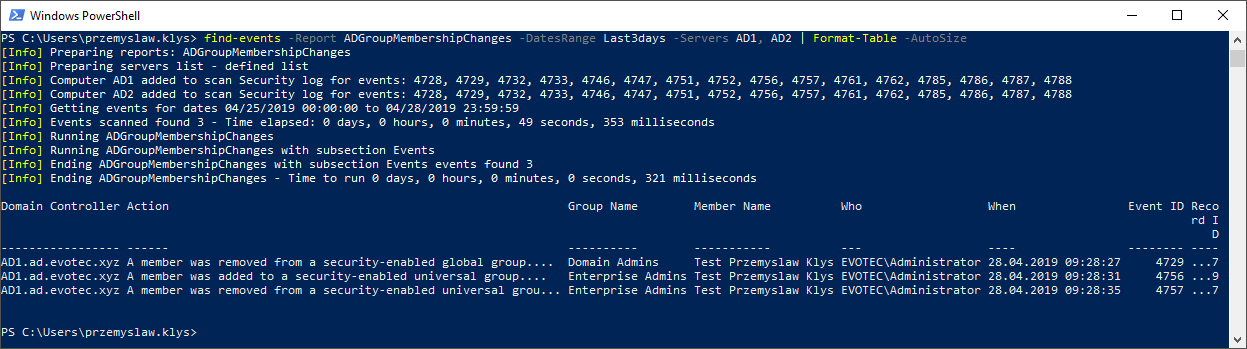
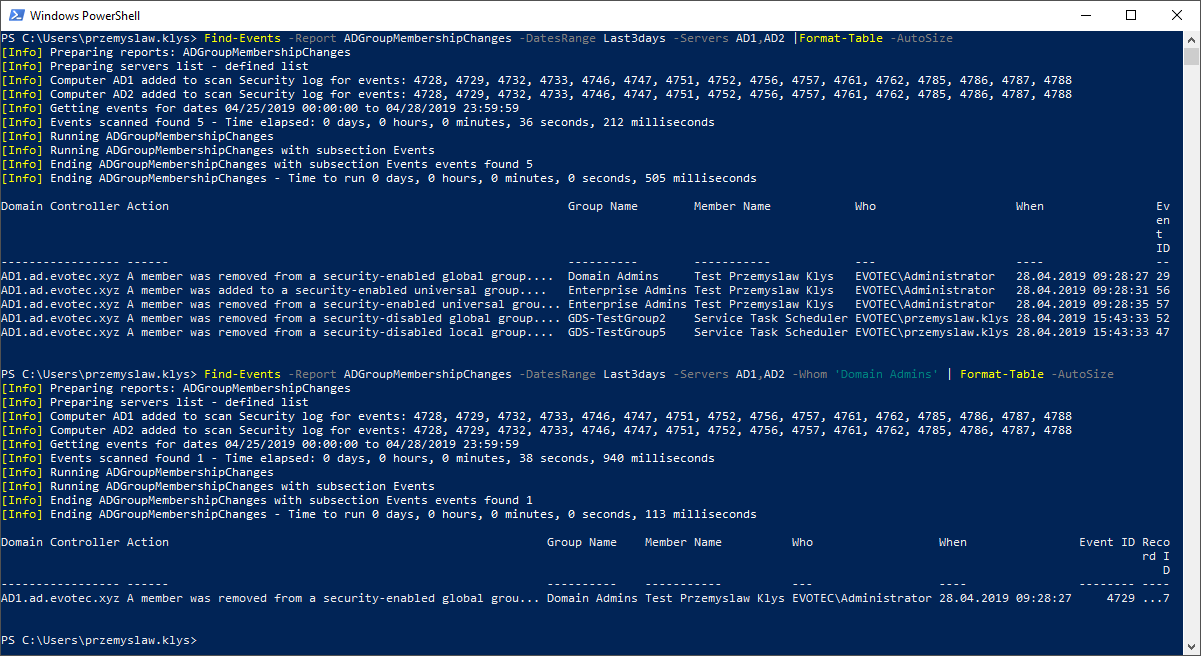
find-events -Report ADGroupMembershipChanges -DatesRange Last3days -Servers AD1, AD2 | Format-Table -AutoSize
As you see above a lot more Event ID's were covered. Since there are lots of Group Membership types, we had to include 4728, 4729, 4732, 4733, 4746, 4747, 4751, 4752, 4756, 4757, 4761, 4762, 4785, 4786, 4787, 4788 event id in Security Log to get all required information. This gives as Security Group Changes, Distribution Group Changes, Local Group Changes and so on. We also now know that user Administrator first removed Test Przemyslaw Klys from Domain Admins, then added user to Enterprise Admins and next deleted user from Enterprise Admins. All those changes are critical to infrastructure. Let's run another test. This time we're asking for both Group Membership Changes and User Changes at the same time.
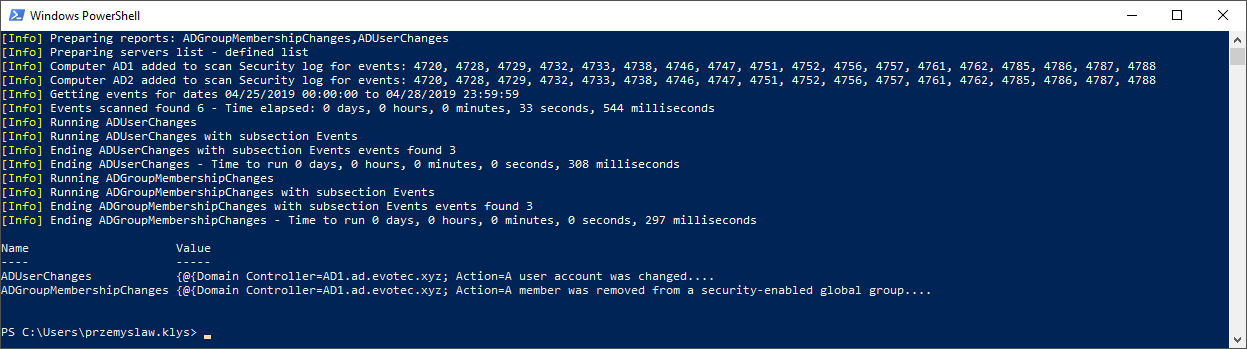
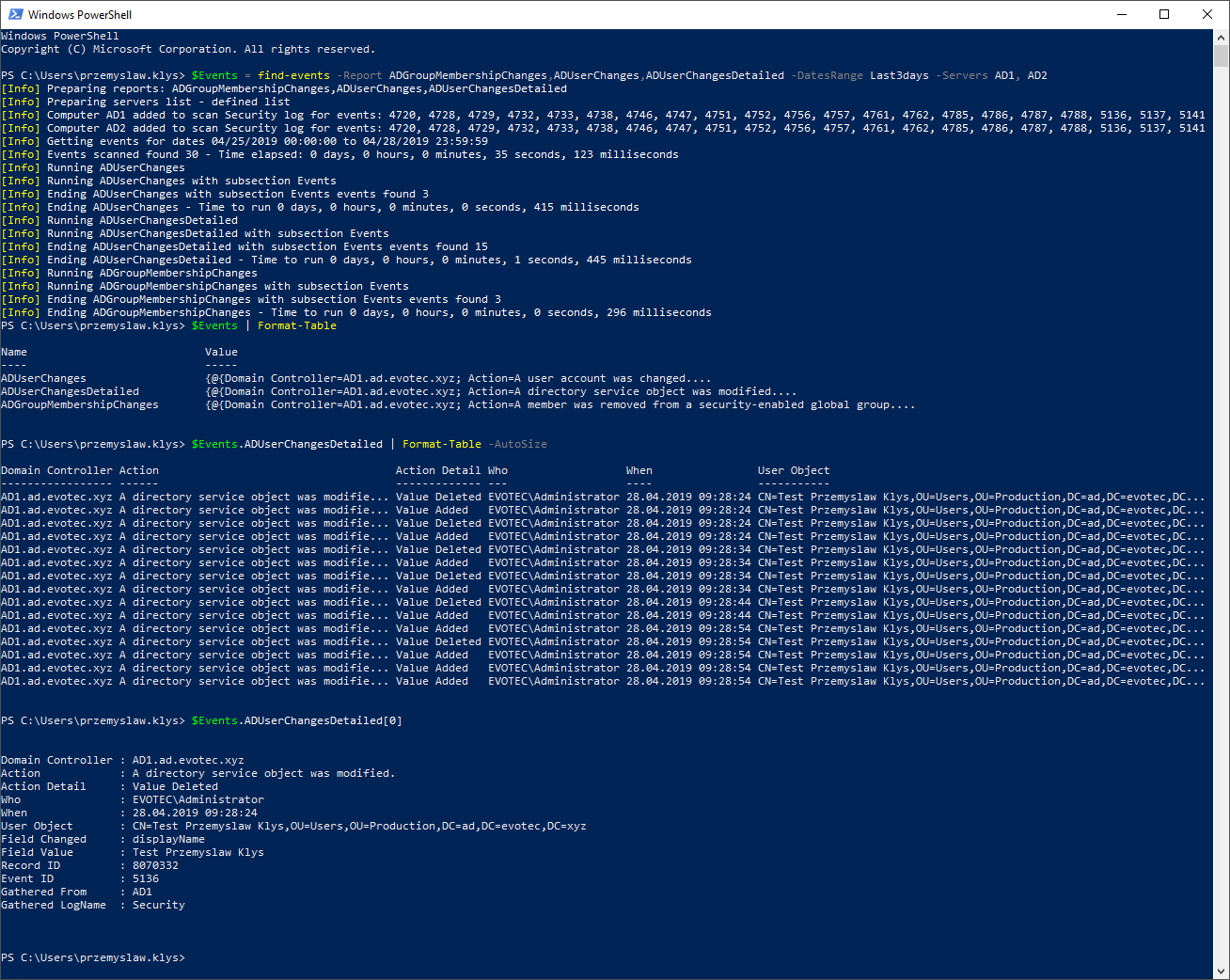
find-events -Report ADGroupMembershipChanges,ADUserChanges -DatesRange Last3days -Servers AD1, AD2 | Format-Table -AutoSize
It doesn't look the same right? Well, when you ask command to deliver multiple types of events, it returns a custom hashtable instead of Array of events. It's because each event type has different columns, different needs for data and putting it together in one large basket may be confusing to read. To get proper events data you can use code like below
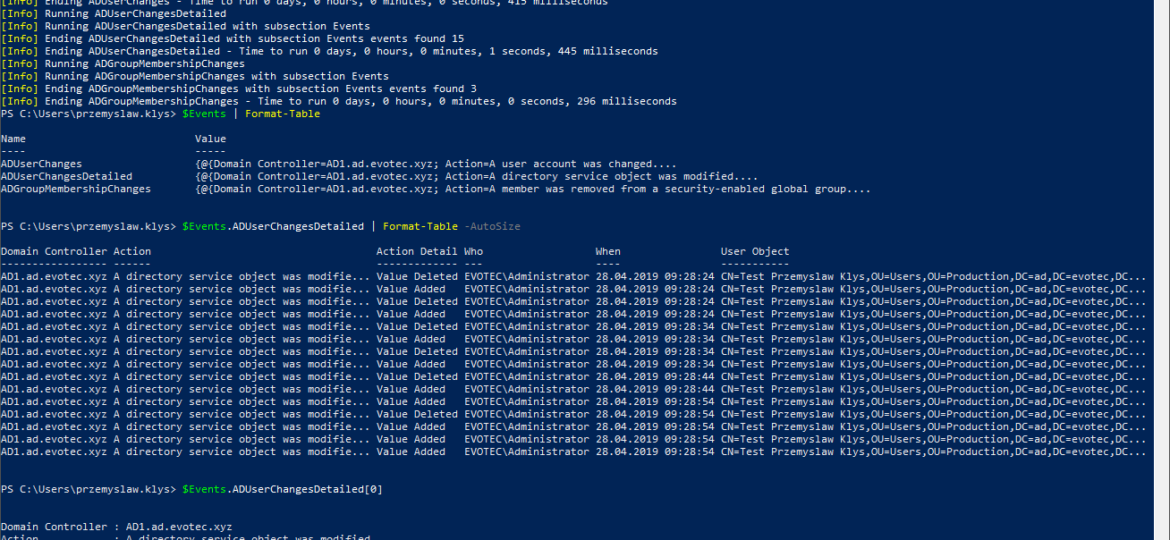
$Events = find-events -Report ADGroupMembershipChanges,ADUserChanges,ADUserChangesDetailed -DatesRange Last3days -Servers AD1, AD2 $Events | Format-Table $Events.ADUserChangesDetailed | Format-Table -AutoSize $Events.ADUserChangesDetailed[0]
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\przemyslaw.klys> $Events = find-events -Report ADGroupMembershipChanges,ADUserChanges,ADUserChangesDetailed -DatesRange Last3days -Servers AD1, AD2
[Info] Preparing reports: ADGroupMembershipChanges,ADUserChanges,ADUserChangesDetailed
[Info] Preparing servers list - defined list
[Info] Computer AD1 added to scan Security log for events: 4720, 4728, 4729, 4732, 4733, 4738, 4746, 4747, 4751, 4752, 4756, 4757, 4761, 4762, 4785, 4786, 4787, 4788, 5136, 5137, 5141
[Info] Computer AD2 added to scan Security log for events: 4720, 4728, 4729, 4732, 4733, 4738, 4746, 4747, 4751, 4752, 4756, 4757, 4761, 4762, 4785, 4786, 4787, 4788, 5136, 5137, 5141
[Info] Getting events for dates 04/25/2019 00:00:00 to 04/28/2019 23:59:59
[Info] Events scanned found 30 - Time elapsed: 0 days, 0 hours, 0 minutes, 35 seconds, 123 milliseconds
[Info] Running ADUserChanges
[Info] Running ADUserChanges with subsection Events
[Info] Ending ADUserChanges with subsection Events events found 3
[Info] Ending ADUserChanges - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 415 milliseconds
[Info] Running ADUserChangesDetailed
[Info] Running ADUserChangesDetailed with subsection Events
[Info] Ending ADUserChangesDetailed with subsection Events events found 15
[Info] Ending ADUserChangesDetailed - Time to run 0 days, 0 hours, 0 minutes, 1 seconds, 445 milliseconds
[Info] Running ADGroupMembershipChanges
[Info] Running ADGroupMembershipChanges with subsection Events
[Info] Ending ADGroupMembershipChanges with subsection Events events found 3
[Info] Ending ADGroupMembershipChanges - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 296 milliseconds
PS C:\Users\przemyslaw.klys> $Events | Format-Table
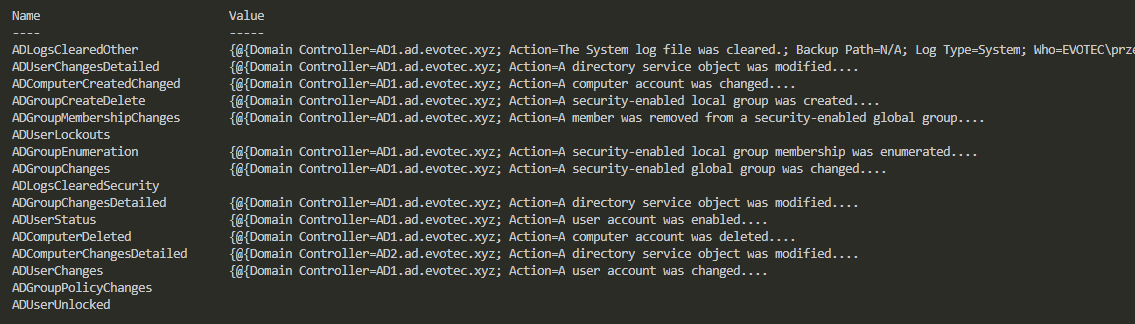
Name Value
---- -----
ADUserChanges {@{Domain Controller=AD1.ad.evotec.xyz; Action=A user account was changed....
ADUserChangesDetailed {@{Domain Controller=AD1.ad.evotec.xyz; Action=A directory service object was modified....
ADGroupMembershipChanges {@{Domain Controller=AD1.ad.evotec.xyz; Action=A member was removed from a security-enabled global group....
PS C:\Users\przemyslaw.klys> $Events.ADUserChangesDetailed | Format-Table -AutoSize
Domain Controller Action Action Detail Who When User Object
----------------- ------ ------------- --- ---- -----------
AD1.ad.evotec.xyz A directory service object was modifie... Value Deleted EVOTEC\Administrator 28.04.2019 09:28:24 CN=Test Przemyslaw Klys,OU=Users,OU=Production,DC=ad,DC=evotec,DC...
AD1.ad.evotec.xyz A directory service object was modifie... Value Added EVOTEC\Administrator 28.04.2019 09:28:24 CN=Test Przemyslaw Klys,OU=Users,OU=Production,DC=ad,DC=evotec,DC...
AD1.ad.evotec.xyz A directory service object was modifie... Value Deleted EVOTEC\Administrator 28.04.2019 09:28:24 CN=Test Przemyslaw Klys,OU=Users,OU=Production,DC=ad,DC=evotec,DC...
AD1.ad.evotec.xyz A directory service object was modifie... Value Added EVOTEC\Administrator 28.04.2019 09:28:24 CN=Test Przemyslaw Klys,OU=Users,OU=Production,DC=ad,DC=evotec,DC...
AD1.ad.evotec.xyz A directory service object was modifie... Value Deleted EVOTEC\Administrator 28.04.2019 09:28:34 CN=Test Przemyslaw Klys,OU=Users,OU=Production,DC=ad,DC=evotec,DC...
AD1.ad.evotec.xyz A directory service object was modifie... Value Added EVOTEC\Administrator 28.04.2019 09:28:34 CN=Test Przemyslaw Klys,OU=Users,OU=Production,DC=ad,DC=evotec,DC...
AD1.ad.evotec.xyz A directory service object was modifie... Value Deleted EVOTEC\Administrator 28.04.2019 09:28:34 CN=Test Przemyslaw Klys,OU=Users,OU=Production,DC=ad,DC=evotec,DC...
AD1.ad.evotec.xyz A directory service object was modifie... Value Added EVOTEC\Administrator 28.04.2019 09:28:34 CN=Test Przemyslaw Klys,OU=Users,OU=Production,DC=ad,DC=evotec,DC...
AD1.ad.evotec.xyz A directory service object was modifie... Value Deleted EVOTEC\Administrator 28.04.2019 09:28:44 CN=Test Przemyslaw Klys,OU=Users,OU=Production,DC=ad,DC=evotec,DC...
AD1.ad.evotec.xyz A directory service object was modifie... Value Added EVOTEC\Administrator 28.04.2019 09:28:44 CN=Test Przemyslaw Klys,OU=Users,OU=Production,DC=ad,DC=evotec,DC...
AD1.ad.evotec.xyz A directory service object was modifie... Value Added EVOTEC\Administrator 28.04.2019 09:28:54 CN=Test Przemyslaw Klys,OU=Users,OU=Production,DC=ad,DC=evotec,DC...
AD1.ad.evotec.xyz A directory service object was modifie... Value Deleted EVOTEC\Administrator 28.04.2019 09:28:54 CN=Test Przemyslaw Klys,OU=Users,OU=Production,DC=ad,DC=evotec,DC...
AD1.ad.evotec.xyz A directory service object was modifie... Value Added EVOTEC\Administrator 28.04.2019 09:28:54 CN=Test Przemyslaw Klys,OU=Users,OU=Production,DC=ad,DC=evotec,DC...
AD1.ad.evotec.xyz A directory service object was modifie... Value Added EVOTEC\Administrator 28.04.2019 09:28:54 CN=Test Przemyslaw Klys,OU=Users,OU=Production,DC=ad,DC=evotec,DC...
AD1.ad.evotec.xyz A directory service object was modifie... Value Added EVOTEC\Administrator 28.04.2019 09:28:54 CN=Test Przemyslaw Klys,OU=Users,OU=Production,DC=ad,DC=evotec,DC...
PS C:\Users\przemyslaw.klys> $Events.ADUserChangesDetailed[0]
Domain Controller : AD1.ad.evotec.xyz
Action : A directory service object was modified.
Action Detail : Value Deleted
Who : EVOTEC\Administrator
When : 28.04.2019 09:28:24
User Object : CN=Test Przemyslaw Klys,OU=Users,OU=Production,DC=ad,DC=evotec,DC=xyz
Field Changed : displayName
Field Value : Test Przemyslaw Klys
Record ID : 8070332
Event ID : 5136
Gathered From : AD1
Gathered LogName : Security
First, we made a scan of three different types of events. Then we displayed custom hashtable and finally, we're accessing each property of hashtable that contains an Array of events. Of course, using Format-Table doesn't show all fields, as those do not fit the screen, so I've used the first element of an array to show detailed user change with all fields. Additional parameter that can be useful for day to day use is DetectDC. This parameter is taken instead of Servers parameter. It forces Find-Events to make a scan each domain controller in each domain within Active Directory Forest.
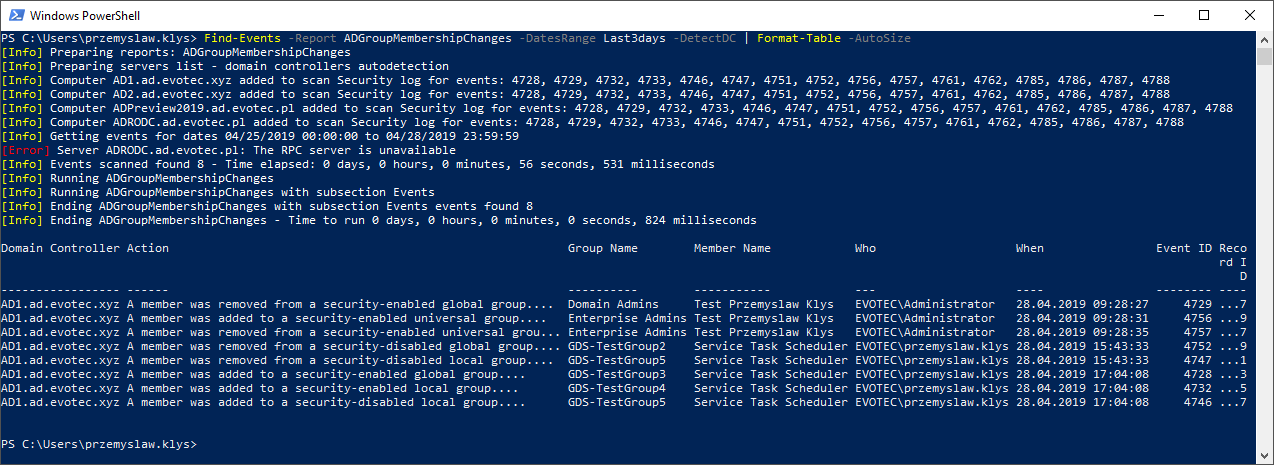
Find-Events -Report ADGroupMembershipChanges -DatesRange Last3days -DetectDC | Format-Table -AutoSize
PS C:\Users\przemyslaw.klys> Find-Events -Report ADGroupMembershipChanges -DatesRange Last3days -DetectDC | Format-Table -AutoSize [Info] Preparing reports: ADGroupMembershipChanges [Info] Preparing servers list - domain controllers autodetection [Info] Computer AD1.ad.evotec.xyz added to scan Security log for events: 4728, 4729, 4732, 4733, 4746, 4747, 4751, 4752, 4756, 4757, 4761, 4762, 4785, 4786, 4787, 4788 [Info] Computer AD2.ad.evotec.xyz added to scan Security log for events: 4728, 4729, 4732, 4733, 4746, 4747, 4751, 4752, 4756, 4757, 4761, 4762, 4785, 4786, 4787, 4788 [Info] Computer ADPreview2019.ad.evotec.pl added to scan Security log for events: 4728, 4729, 4732, 4733, 4746, 4747, 4751, 4752, 4756, 4757, 4761, 4762, 4785, 4786, 4787, 4788 [Info] Computer ADRODC.ad.evotec.pl added to scan Security log for events: 4728, 4729, 4732, 4733, 4746, 4747, 4751, 4752, 4756, 4757, 4761, 4762, 4785, 4786, 4787, 4788 [Info] Getting events for dates 04/25/2019 00:00:00 to 04/28/2019 23:59:59 [Error] Server ADRODC.ad.evotec.pl: The RPC server is unavailable [Info] Events scanned found 8 - Time elapsed: 0 days, 0 hours, 0 minutes, 56 seconds, 531 milliseconds [Info] Running ADGroupMembershipChanges [Info] Running ADGroupMembershipChanges with subsection Events [Info] Ending ADGroupMembershipChanges with subsection Events events found 8 [Info] Ending ADGroupMembershipChanges - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 824 milliseconds
💡 Find-Events – Limiting output?
Now, if you aren't excited about this command by now I'm really disappointed in you. But maybe this will win you over?
$Events = Find-Events -Report ADGroupMembershipChanges -DatesRange Last3days -Servers 'AD1', 'AD2' -Whom 'Domain Admins' -Verbose $Events | Format-Table -AutoSize
[Info] Preparing reports: ADGroupMembershipChanges
[Info] Preparing servers list - defined list
[Info] Computer AD1 added to scan Security log for events: 4728, 4729, 4732, 4733, 4746, 4747, 4751, 4752, 4756, 4757, 4761, 4762, 4785, 4786, 4787, 4788
[Info] Computer AD2 added to scan Security log for events: 4728, 4729, 4732, 4733, 4746, 4747, 4751, 4752, 4756, 4757, 4761, 4762, 4785, 4786, 4787, 4788
[Info] Getting events for dates 04/25/2019 00:00:00 to 04/28/2019 23:59:59
VERBOSE: Get-Events - Preparing data to scan computer AD1
VERBOSE: Get-Events - Filter parameters provided EndTime = 04/28/2019 23:59:59
VERBOSE: Get-Events - Filter parameters provided LogName = Security
VERBOSE: Get-Events - Filter parameters provided StartTime = 04/25/2019 00:00:00
VERBOSE: Get-Events - Filter parameters provided NamedDataFilter with SubKey TargetUserName = Domain Admins
VERBOSE: Get-Events - Events to process in Total (unique): 16
VERBOSE: Get-Events - Events to process in Total ID: 4728, 4729, 4732, 4733, 4746, 4747, 4751, 4752, 4756, 4757, 4761, 4762, 4785, 4786, 4787, 4788
VERBOSE: Get-Events - Preparing data to scan computer AD2
VERBOSE: Get-Events - Filter parameters provided EndTime = 04/28/2019 23:59:59
VERBOSE: Get-Events - Filter parameters provided LogName = Security
VERBOSE: Get-Events - Filter parameters provided StartTime = 04/25/2019 00:00:00
VERBOSE: Get-Events - Filter parameters provided NamedDataFilter with SubKey TargetUserName = Domain Admins
VERBOSE: Get-Events - Events to process in Total (unique): 16
VERBOSE: Get-Events - Events to process in Total ID: 4728, 4729, 4732, 4733, 4746, 4747, 4751, 4752, 4756, 4757, 4761, 4762, 4785, 4786, 4787, 4788
VERBOSE: Get-Events - Running query with parallel enabled...
VERBOSE: Get-Events -------------START---------------------
VERBOSE: Get-Events - Inside AD1 for Events ID: 4728 4729 4732 4733 4746 4747 4751 4752 4756 4757 4761 4762 4785 4786 4787 4788
VERBOSE: Get-Events - Inside AD1 for Events LogName: Security
VERBOSE: Get-Events - Inside AD1 for Events RecordID:
VERBOSE: Get-Events - Inside AD1 for Events Oldest: False
VERBOSE: Get-Events - Inside AD1 for Events Max Events: 0
VERBOSE: Get-Events - Inside AD1 - Custom FilterXML:
VERBOSE: Get-Events - Inside AD1 Events found 1
VERBOSE: Get-Events - Inside AD1 Processing events...
VERBOSE: Get-Events - Inside AD1 Time to generate 0 hours, 0 minutes, 33 seconds, 688 milliseconds
VERBOSE: Get-Events --------------END----------------------
VERBOSE: Get-Events -------------START---------------------
VERBOSE: Get-Events - Inside AD2 for Events ID: 4728 4729 4732 4733 4746 4747 4751 4752 4756 4757 4761 4762 4785 4786 4787 4788
VERBOSE: Get-Events - Inside AD2 for Events LogName: Security
VERBOSE: Get-Events - Inside AD2 for Events RecordID:
VERBOSE: Get-Events - Inside AD2 for Events Oldest: False
VERBOSE: Get-Events - Inside AD2 for Events Max Events: 0
VERBOSE: Get-Events - Inside AD2 - Custom FilterXML:
VERBOSE: Get-Events - Inside AD2 No events found.
VERBOSE: Get-Events - Inside AD2 Time to generate 0 hours, 0 minutes, 47 seconds, 15 milliseconds
VERBOSE: Get-Events --------------END----------------------
VERBOSE: Get-Events - Overall errors: 0
VERBOSE: Get-Events - Overall events processed in total for the report: 1
VERBOSE: Get-Events - Overall time to generate 0 hours, 0 minutes, 47 seconds, 129 milliseconds
VERBOSE: Get-Events - Overall events processing end
[Info] Events scanned found 1 - Time elapsed: 0 days, 0 hours, 0 minutes, 47 seconds, 158 milliseconds
[Info] Running ADGroupMembershipChanges
[Info] Running ADGroupMembershipChanges with subsection Events
[Info] Ending ADGroupMembershipChanges with subsection Events events found 1
[Info] Ending ADGroupMembershipChanges - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 115 milliseconds
Alternatively this?
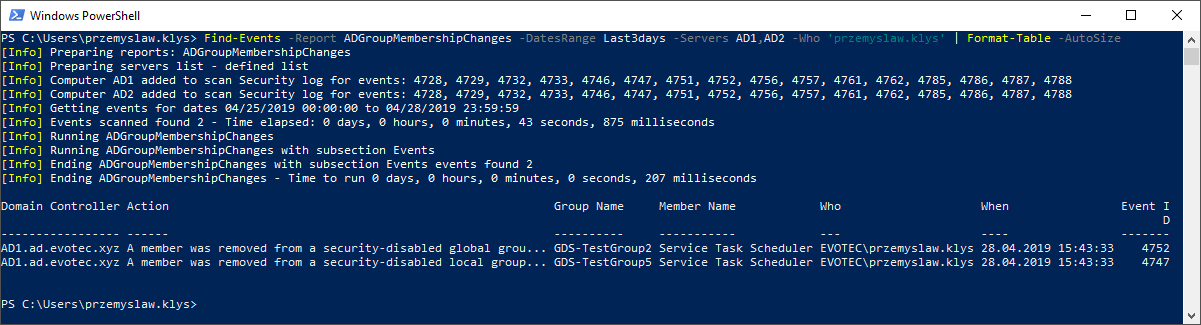
$Events = Find-Events -Report ADGroupMembershipChanges -DatesRange Last3days -Servers 'AD1', 'AD2' -Who 'przemyslaw.klys' -Verbose $Events | Format-Table -AutoSize
To make it clear, the search for user or group is done on XPath / XML level. It queries for that information directly into Event Log. This means that if you're searching for particular user actions, you can filter it out on Query Level. And that means a shorter time to ask for events. You see, the more direct the query, the faster the return of data. There is no post-filtering of data. Post-processing you see on the screen when you don't use Quiet switch is strictly related to translating names, cleaning up and so on. It's a quite fast process. There are also negative versions of Who, Whom. Those are NotWho, NotWhom.
💡 Installation / Updates
This command is part of PSWinReportingV2 module. If you have used PSWinReporting before there's a new version of it. I've decided that two versions can coexist together until PSWinReportingV2 is mature enough to take over reporting totally from PSWinReporting. Since PSWinReportingV2 is a complete rewrite, config changes are significant, and they allow for a lot of modifications and control, including monitoring ADConnect, File Servers or any other server type you want. But that's a story for another article. Today you have to enjoy Find-Events command, or rather some bits and pieces of it, as it has more Powers that are currently not described here.
Install-Module PSWinReportingV2 -Force
After you install that module Find-Events command will be available for you. If you like that module please take a moment and leave a Star on GitHub for my project. I really appreciate it. Please keep in mind that PSWinReportingV2 is based on PSEventViewer and PSSharedGoods. When you install PSWinReportingV2 both those modules will be installed along, and are required for the command to work. PSEventViewer is a wrapper around Get-WinEvent and it's a brain behind Find-Events command. It's responsible for parallel scans, solving Get-WinEvents limits and XPATH generation.
💡 Asking Find-Events for multiple reports
There's one more thing you should know. It's much faster to ask for events once, and then filter it out, then question 5 times separately.
Import-Module .\PSWinReportingV2.psd1 -Force
$Reports = @(
'ADUserChanges'
'ADUserChangesDetailed'
'ADComputerChangesDetailed'
'ADUserStatus'
'ADUserLockouts'
#ADUserLogon
'ADUserUnlocked'
'ADComputerCreatedChanged'
'ADComputerDeleted'
#'ADUserLogonKerberos'
'ADGroupMembershipChanges'
'ADGroupEnumeration'
'ADGroupChanges'
'ADGroupCreateDelete'
'ADGroupChangesDetailed'
'ADGroupPolicyChanges'
'ADLogsClearedSecurity'
'ADLogsClearedOther'
#ADEventsReboots
)
$Events = Find-Events -Report $Reports -DatesRange Last3days -Servers 'AD1', 'AD2' -Verbose
[Info] Preparing reports: ADUserChanges,ADUserChangesDetailed,ADComputerChangesDetailed,ADUserStatus,ADUserLockouts,ADUserUnlocked,ADComputerCreatedChanged,ADComputerDeleted,ADGroupMembershipChanges,ADGroupEnumeration,ADGroupChanges,ADGroupCreateDelete,ADGroupChangesDetailed,ADGroupPolicyChanges,ADLogsClearedSecurity,ADLogsClearedOther [Info] Preparing servers list - defined list [Info] Computer AD1 added to scan Security log for events: 1102, 1105, 4720, 4722, 4723, 4724, 4725, 4726, 4727, 4728, 4729, 4730, 4731, 4732, 4733, 4734, 4735, 4737, 4738, 4740, 4741, 4742, 4743, 4744, 4745, 4746, 4747, 4748, 4749, 4750, 4751, 4752, 4753, 4754, 4756, 4757, 4758, 4759, 4760, 4761, 4762, 4763, 4764, 4767, 4784, 4785, 4786, 4787, 4788, 4791, 4798, 4799, 5136, 5137, 5141 [Info] Computer AD2 added to scan Security log for events: 1102, 1105, 4720, 4722, 4723, 4724, 4725, 4726, 4727, 4728, 4729, 4730, 4731, 4732, 4733, 4734, 4735, 4737, 4738, 4740, 4741, 4742, 4743, 4744, 4745, 4746, 4747, 4748, 4749, 4750, 4751, 4752, 4753, 4754, 4756, 4757, 4758, 4759, 4760, 4761, 4762, 4763, 4764, 4767, 4784, 4785, 4786, 4787, 4788, 4791, 4798, 4799, 5136, 5137, 5141 [Info] Computer AD1 added to scan System log for events: 104 [Info] Computer AD2 added to scan System log for events: 104 [Info] Getting events for dates 04/25/2019 00:00:00 to 04/28/2019 23:59:59 VERBOSE: Get-Events - Preparing data to scan computer AD1 VERBOSE: Get-Events - Filter parameters provided EndTime = 04/28/2019 23:59:59 VERBOSE: Get-Events - Filter parameters provided LogName = Security VERBOSE: Get-Events - Filter parameters provided StartTime = 04/25/2019 00:00:00 VERBOSE: Get-Events - Events to process in Total (unique): 55 VERBOSE: Get-Events - Events to process in Total ID: 1102, 1105, 4720, 4722, 4723, 4724, 4725, 4726, 4727, 4728, 4729, 4730, 4731, 4732, 4733, 4734, 4735, 4737, 4738, 4740, 4741, 4742, 4743, 4744, 4745, 4746, 4747, 4748, 4749, 4750, 4751, 4752, 4753, 4754, 4756, 4757, 4758, 4759, 4760, 4761, 4762, 4763, 4764, 4767, 4784, 4785, 4786, 4787, 4788, 4791, 4798, 4799, 5136, 5137, 5141 VERBOSE: Get-Events - There are more events to process then 22, split will be required. VERBOSE: Get-Events - Preparing data to scan computer AD2 VERBOSE: Get-Events - Filter parameters provided EndTime = 04/28/2019 23:59:59 VERBOSE: Get-Events - Filter parameters provided LogName = Security VERBOSE: Get-Events - Filter parameters provided StartTime = 04/25/2019 00:00:00 VERBOSE: Get-Events - Events to process in Total (unique): 55 VERBOSE: Get-Events - Events to process in Total ID: 1102, 1105, 4720, 4722, 4723, 4724, 4725, 4726, 4727, 4728, 4729, 4730, 4731, 4732, 4733, 4734, 4735, 4737, 4738, 4740, 4741, 4742, 4743, 4744, 4745, 4746, 4747, 4748, 4749, 4750, 4751, 4752, 4753, 4754, 4756, 4757, 4758, 4759, 4760, 4761, 4762, 4763, 4764, 4767, 4784, 4785, 4786, 4787, 4788, 4791, 4798, 4799, 5136, 5137, 5141 VERBOSE: Get-Events - There are more events to process then 22, split will be required. VERBOSE: Get-Events - Preparing data to scan computer AD1 VERBOSE: Get-Events - Filter parameters provided EndTime = 04/28/2019 23:59:59 VERBOSE: Get-Events - Filter parameters provided LogName = System VERBOSE: Get-Events - Filter parameters provided StartTime = 04/25/2019 00:00:00 VERBOSE: Get-Events - Events to process in Total (unique): 1 VERBOSE: Get-Events - Events to process in Total ID: 104 VERBOSE: Get-Events - Preparing data to scan computer AD2 VERBOSE: Get-Events - Filter parameters provided EndTime = 04/28/2019 23:59:59 VERBOSE: Get-Events - Filter parameters provided LogName = System VERBOSE: Get-Events - Filter parameters provided StartTime = 04/25/2019 00:00:00 VERBOSE: Get-Events - Events to process in Total (unique): 1 VERBOSE: Get-Events - Events to process in Total ID: 104 VERBOSE: Get-Events - Running query with parallel enabled... VERBOSE: Get-Events -------------START--------------------- VERBOSE: Get-Events - Inside AD1 for Events ID: 104 VERBOSE: Get-Events - Inside AD1 for Events LogName: System VERBOSE: Get-Events - Inside AD1 for Events RecordID: VERBOSE: Get-Events - Inside AD1 for Events Oldest: False VERBOSE: Get-Events - Inside AD1 for Events Max Events: 0 VERBOSE: Get-Events - Inside AD1 Data in FilterHashTable EndTime 04/28/2019 23:59:59 VERBOSE: Get-Events - Inside AD1 Data in FilterHashTable LogName System VERBOSE: Get-Events - Inside AD1 Data in FilterHashTable Id 104 VERBOSE: Get-Events - Inside AD1 Data in FilterHashTable StartTime 04/25/2019 00:00:00 VERBOSE: Constructed structured query:. VERBOSE: Get-Events - Inside AD1 Events found 2 VERBOSE: Get-Events - Inside AD1 Processing events... VERBOSE: Get-Events - Inside AD1 Time to generate 0 hours, 0 minutes, 0 seconds, 77 milliseconds VERBOSE: Get-Events --------------END---------------------- VERBOSE: Get-Events -------------START--------------------- VERBOSE: Get-Events - Inside AD2 for Events ID: 104 VERBOSE: Get-Events - Inside AD2 for Events LogName: System VERBOSE: Get-Events - Inside AD2 for Events RecordID: VERBOSE: Get-Events - Inside AD2 for Events Oldest: False VERBOSE: Get-Events - Inside AD2 for Events Max Events: 0 VERBOSE: Get-Events - Inside AD2 Data in FilterHashTable EndTime 04/28/2019 23:59:59 VERBOSE: Get-Events - Inside AD2 Data in FilterHashTable LogName System VERBOSE: Get-Events - Inside AD2 Data in FilterHashTable Id 104 VERBOSE: Get-Events - Inside AD2 Data in FilterHashTable StartTime 04/25/2019 00:00:00 VERBOSE: Constructed structured query: . VERBOSE: Get-Events - Inside AD2 No events found. VERBOSE: Get-Events - Inside AD2 Time to generate 0 hours, 0 minutes, 5 seconds, 628 milliseconds VERBOSE: Get-Events --------------END---------------------- VERBOSE: Get-Events -------------START--------------------- VERBOSE: Get-Events - Inside AD1 for Events ID: 4743 4744 4745 4746 4747 4748 4749 4750 4751 4752 4753 4754 4756 4757 4758 4759 4760 4761 4762 4763 4764 4767 VERBOSE: Get-Events - Inside AD1 for Events LogName: Security VERBOSE: Get-Events - Inside AD1 for Events RecordID: VERBOSE: Get-Events - Inside AD1 for Events Oldest: False VERBOSE: Get-Events - Inside AD1 for Events Max Events: 0 VERBOSE: Get-Events - Inside AD1 Data in FilterHashTable EndTime 04/28/2019 23:59:59 VERBOSE: Get-Events - Inside AD1 Data in FilterHashTable LogName Security VERBOSE: Get-Events - Inside AD1 Data in FilterHashTable Id 4743 4744 4745 4746 4747 4748 4749 4750 4751 4752 4753 4754 4756 4757 4758 4759 4760 4761 4762 4763 4764 4767 VERBOSE: Get-Events - Inside AD1 Data in FilterHashTable StartTime 04/25/2019 00:00:00 VERBOSE: Constructed structured query: . VERBOSE: Get-Events - Inside AD1 Events found 9 VERBOSE: Get-Events - Inside AD1 Processing events... VERBOSE: Get-Events - Inside AD1 Time to generate 0 hours, 0 minutes, 25 seconds, 392 milliseconds VERBOSE: Get-Events --------------END---------------------- VERBOSE: Get-Events -------------START--------------------- VERBOSE: Get-Events - Inside AD1 for Events ID: 1102 1105 4720 4722 4723 4724 4725 4726 4727 4728 4729 4730 4731 4732 4733 4734 4735 4737 4738 4740 4741 4742 VERBOSE: Get-Events - Inside AD1 for Events LogName: Security VERBOSE: Get-Events - Inside AD1 for Events RecordID: VERBOSE: Get-Events - Inside AD1 for Events Oldest: False VERBOSE: Get-Events - Inside AD1 for Events Max Events: 0 VERBOSE: Get-Events - Inside AD1 Data in FilterHashTable EndTime 04/28/2019 23:59:59 VERBOSE: Get-Events - Inside AD1 Data in FilterHashTable LogName Security VERBOSE: Get-Events - Inside AD1 Data in FilterHashTable Id 1102 1105 4720 4722 4723 4724 4725 4726 4727 4728 4729 4730 4731 4732 4733 4734 4735 4737 4738 4740 4741 4742 VERBOSE: Get-Events - Inside AD1 Data in FilterHashTable StartTime 04/25/2019 00:00:00 VERBOSE: Constructed structured query: . VERBOSE: Get-Events - Inside AD1 Events found 26 VERBOSE: Get-Events - Inside AD1 Processing events... VERBOSE: Get-Events - Inside AD1 Time to generate 0 hours, 0 minutes, 25 seconds, 655 milliseconds VERBOSE: Get-Events --------------END---------------------- VERBOSE: Get-Events -------------START--------------------- VERBOSE: Get-Events - Inside AD1 for Events ID: 4784 4785 4786 4787 4788 4791 4798 4799 5136 5137 5141 VERBOSE: Get-Events - Inside AD1 for Events LogName: Security VERBOSE: Get-Events - Inside AD1 for Events RecordID: VERBOSE: Get-Events - Inside AD1 for Events Oldest: False VERBOSE: Get-Events - Inside AD1 for Events Max Events: 0 VERBOSE: Get-Events - Inside AD1 Data in FilterHashTable EndTime 04/28/2019 23:59:59 VERBOSE: Get-Events - Inside AD1 Data in FilterHashTable LogName Security VERBOSE: Get-Events - Inside AD1 Data in FilterHashTable Id 4784 4785 4786 4787 4788 4791 4798 4799 5136 5137 5141 VERBOSE: Get-Events - Inside AD1 Data in FilterHashTable StartTime 04/25/2019 00:00:00 VERBOSE: Constructed structured query: . VERBOSE: Get-Events - Inside AD1 Events found 150 VERBOSE: Get-Events - Inside AD1 Processing events... VERBOSE: Get-Events - Inside AD1 Time to generate 0 hours, 0 minutes, 31 seconds, 507 milliseconds VERBOSE: Get-Events --------------END---------------------- VERBOSE: Get-Events -------------START--------------------- VERBOSE: Get-Events - Inside AD2 for Events ID: 4743 4744 4745 4746 4747 4748 4749 4750 4751 4752 4753 4754 4756 4757 4758 4759 4760 4761 4762 4763 4764 4767 VERBOSE: Get-Events - Inside AD2 for Events LogName: Security VERBOSE: Get-Events - Inside AD2 for Events RecordID: VERBOSE: Get-Events - Inside AD2 for Events Oldest: False VERBOSE: Get-Events - Inside AD2 for Events Max Events: 0 VERBOSE: Get-Events - Inside AD2 Data in FilterHashTable EndTime 04/28/2019 23:59:59 VERBOSE: Get-Events - Inside AD2 Data in FilterHashTable LogName Security VERBOSE: Get-Events - Inside AD2 Data in FilterHashTable Id 4743 4744 4745 4746 4747 4748 4749 4750 4751 4752 4753 4754 4756 4757 4758 4759 4760 4761 4762 4763 4764 4767 VERBOSE: Get-Events - Inside AD2 Data in FilterHashTable StartTime 04/25/2019 00:00:00 VERBOSE: Constructed structured query: . VERBOSE: Get-Events - Inside AD2 No events found. VERBOSE: Get-Events - Inside AD2 Time to generate 0 hours, 0 minutes, 56 seconds, 577 milliseconds VERBOSE: Get-Events --------------END---------------------- VERBOSE: Get-Events -------------START--------------------- VERBOSE: Get-Events - Inside AD2 for Events ID: 1102 1105 4720 4722 4723 4724 4725 4726 4727 4728 4729 4730 4731 4732 4733 4734 4735 4737 4738 4740 4741 4742 VERBOSE: Get-Events - Inside AD2 for Events LogName: Security VERBOSE: Get-Events - Inside AD2 for Events RecordID: VERBOSE: Get-Events - Inside AD2 for Events Oldest: False VERBOSE: Get-Events - Inside AD2 for Events Max Events: 0 VERBOSE: Get-Events - Inside AD2 Data in FilterHashTable EndTime 04/28/2019 23:59:59 VERBOSE: Get-Events - Inside AD2 Data in FilterHashTable LogName Security VERBOSE: Get-Events - Inside AD2 Data in FilterHashTable Id 1102 1105 4720 4722 4723 4724 4725 4726 4727 4728 4729 4730 4731 4732 4733 4734 4735 4737 4738 4740 4741 4742 VERBOSE: Get-Events - Inside AD2 Data in FilterHashTable StartTime 04/25/2019 00:00:00 VERBOSE: Constructed structured query: . VERBOSE: Get-Events - Inside AD2 Events found 1 VERBOSE: Get-Events - Inside AD2 Processing events... VERBOSE: Get-Events - Inside AD2 Time to generate 0 hours, 1 minutes, 2 seconds, 270 milliseconds VERBOSE: Get-Events --------------END---------------------- VERBOSE: Get-Events -------------START--------------------- VERBOSE: Get-Events - Inside AD2 for Events ID: 4784 4785 4786 4787 4788 4791 4798 4799 5136 5137 5141 VERBOSE: Get-Events - Inside AD2 for Events LogName: Security VERBOSE: Get-Events - Inside AD2 for Events RecordID: VERBOSE: Get-Events - Inside AD2 for Events Oldest: False VERBOSE: Get-Events - Inside AD2 for Events Max Events: 0 VERBOSE: Get-Events - Inside AD2 Data in FilterHashTable EndTime 04/28/2019 23:59:59 VERBOSE: Get-Events - Inside AD2 Data in FilterHashTable LogName Security VERBOSE: Get-Events - Inside AD2 Data in FilterHashTable Id 4784 4785 4786 4787 4788 4791 4798 4799 5136 5137 5141 VERBOSE: Get-Events - Inside AD2 Data in FilterHashTable StartTime 04/25/2019 00:00:00 VERBOSE: Constructed structured query: . VERBOSE: Get-Events - Inside AD2 Events found 47 VERBOSE: Get-Events - Inside AD2 Processing events... VERBOSE: Get-Events - Inside AD2 Time to generate 0 hours, 1 minutes, 5 seconds, 841 milliseconds VERBOSE: Get-Events --------------END---------------------- VERBOSE: Get-Events - Overall errors: 0 VERBOSE: Get-Events - Overall events processed in total for the report: 235 VERBOSE: Get-Events - Overall time to generate 0 hours, 1 minutes, 6 seconds, 83 milliseconds VERBOSE: Get-Events - Overall events processing end [Info] Events scanned found 235 - Time elapsed: 0 days, 0 hours, 1 minutes, 6 seconds, 138 milliseconds [Info] Running ADUserChanges [Info] Running ADUserChanges with subsection Events [Info] Ending ADUserChanges with subsection Events events found 9 [Info] Ending ADUserChanges - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 949 milliseconds [Info] Running ADUserChangesDetailed [Info] Running ADUserChangesDetailed with subsection Events [Info] Ending ADUserChangesDetailed with subsection Events events found 30 [Info] Ending ADUserChangesDetailed - Time to run 0 days, 0 hours, 0 minutes, 2 seconds, 997 milliseconds [Info] Running ADComputerChangesDetailed [Info] Running ADComputerChangesDetailed with subsection Events [Info] Ending ADComputerChangesDetailed with subsection Events events found 6 [Info] Ending ADComputerChangesDetailed - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 612 milliseconds [Info] Running ADUserStatus [Info] Running ADUserStatus with subsection Events [Info] Ending ADUserStatus with subsection Events events found 6 [Info] Ending ADUserStatus - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 614 milliseconds [Info] Running ADUserLockouts [Info] Running ADUserLockouts with subsection Events [Info] Ending ADUserLockouts with subsection Events events found 0 [Info] Ending ADUserLockouts - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 14 milliseconds [Info] Running ADUserUnlocked [Info] Running ADUserUnlocked with subsection Events [Info] Ending ADUserUnlocked with subsection Events events found 0 [Info] Ending ADUserUnlocked - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 10 milliseconds [Info] Running ADComputerCreatedChanged [Info] Running ADComputerCreatedChanged with subsection Events [Info] Ending ADComputerCreatedChanged with subsection Events events found 6 [Info] Ending ADComputerCreatedChanged - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 602 milliseconds [Info] Running ADComputerDeleted [Info] Running ADComputerDeleted with subsection Events [Info] Ending ADComputerDeleted with subsection Events events found 1 [Info] Ending ADComputerDeleted - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 117 milliseconds [Info] Running ADGroupMembershipChanges [Info] Running ADGroupMembershipChanges with subsection Events [Info] Ending ADGroupMembershipChanges with subsection Events events found 8 [Info] Ending ADGroupMembershipChanges - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 815 milliseconds [Info] Running ADGroupEnumeration [Info] Running ADGroupEnumeration with subsection Events [Info] Ending ADGroupEnumeration with subsection Events events found 149 [Info] Ending ADGroupEnumeration - Time to run 0 days, 0 hours, 0 minutes, 14 seconds, 615 milliseconds [Info] Running ADGroupChanges [Info] Running ADGroupChanges with subsection Events [Info] Ending ADGroupChanges with subsection Events events found 6 [Info] Ending ADGroupChanges - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 579 milliseconds [Info] Running ADGroupCreateDelete [Info] Running ADGroupCreateDelete with subsection Events [Info] Ending ADGroupCreateDelete with subsection Events events found 0 [Info] Ending ADGroupCreateDelete - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 18 milliseconds [Info] Running ADGroupChangesDetailed [Info] Running ADGroupChangesDetailed with subsection Events [Info] Ending ADGroupChangesDetailed with subsection Events events found 5 [Info] Ending ADGroupChangesDetailed - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 489 milliseconds [Info] Running ADGroupPolicyChanges [Info] Running ADGroupPolicyChanges with subsection Group Policy Name Changes [Info] Ending ADGroupPolicyChanges with subsection Group Policy Name Changes events found 0 [Info] Running ADGroupPolicyChanges with subsection Group Policy Edits [Info] Ending ADGroupPolicyChanges with subsection Group Policy Edits events found 0 [Info] Running ADGroupPolicyChanges with subsection Group Policy Links [Info] Ending ADGroupPolicyChanges with subsection Group Policy Links events found 0 [Info] Ending ADGroupPolicyChanges - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 32 milliseconds [Info] Running ADLogsClearedSecurity [Info] Running ADLogsClearedSecurity with subsection Events [Info] Ending ADLogsClearedSecurity with subsection Events events found 0 [Info] Ending ADLogsClearedSecurity - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 18 milliseconds [Info] Running ADLogsClearedOther [Info] Running ADLogsClearedOther with subsection Events [Info] Ending ADLogsClearedOther with subsection Events events found 2 [Info] Ending ADLogsClearedOther - Time to run 0 days, 0 hours, 0 minutes, 0 seconds, 38 milliseconds
As you can see above, Get-Events (from PSEventViewer) is utilizing its power to get all events, and it does it in just 1 minute and 6 seconds. So even thou we've asked for much more events than we did above we get them in the same amount of time.
One more thing to know, and notice, is that I've skipped three reports. ADUserLogon, ADuserLogonKerberos and ADEventsReboots. The first two reports often contain so much information that getting that information is time-consuming. ADEventsReboots, on the other hand, is useless. I've not spent much time developing that report, so the information there is hardly useful.
💡 Dashimo with Find-Events
Import-Module Dashimo # Install-Module Dashimo -Force
Import-Module PSWinReportingV2 # Install-Module PSWinReportingV2 -Force
$Reports = @(
'ADUserChanges'
'ADUserChangesDetailed'
'ADComputerChangesDetailed'
'ADUserStatus'
'ADUserLockouts'
#ADUserLogon
'ADUserUnlocked'
'ADComputerCreatedChanged'
'ADComputerDeleted'
#'ADUserLogonKerberos'
'ADGroupMembershipChanges'
'ADGroupEnumeration'
'ADGroupChanges'
'ADGroupCreateDelete'
'ADGroupChangesDetailed'
'ADGroupPolicyChanges'
'ADLogsClearedSecurity'
'ADLogsClearedOther'
#ADEventsReboots
)
$Events = Find-Events -Report $Reports -DatesRange Last3days -Servers 'AD1', 'AD2' -Verbose
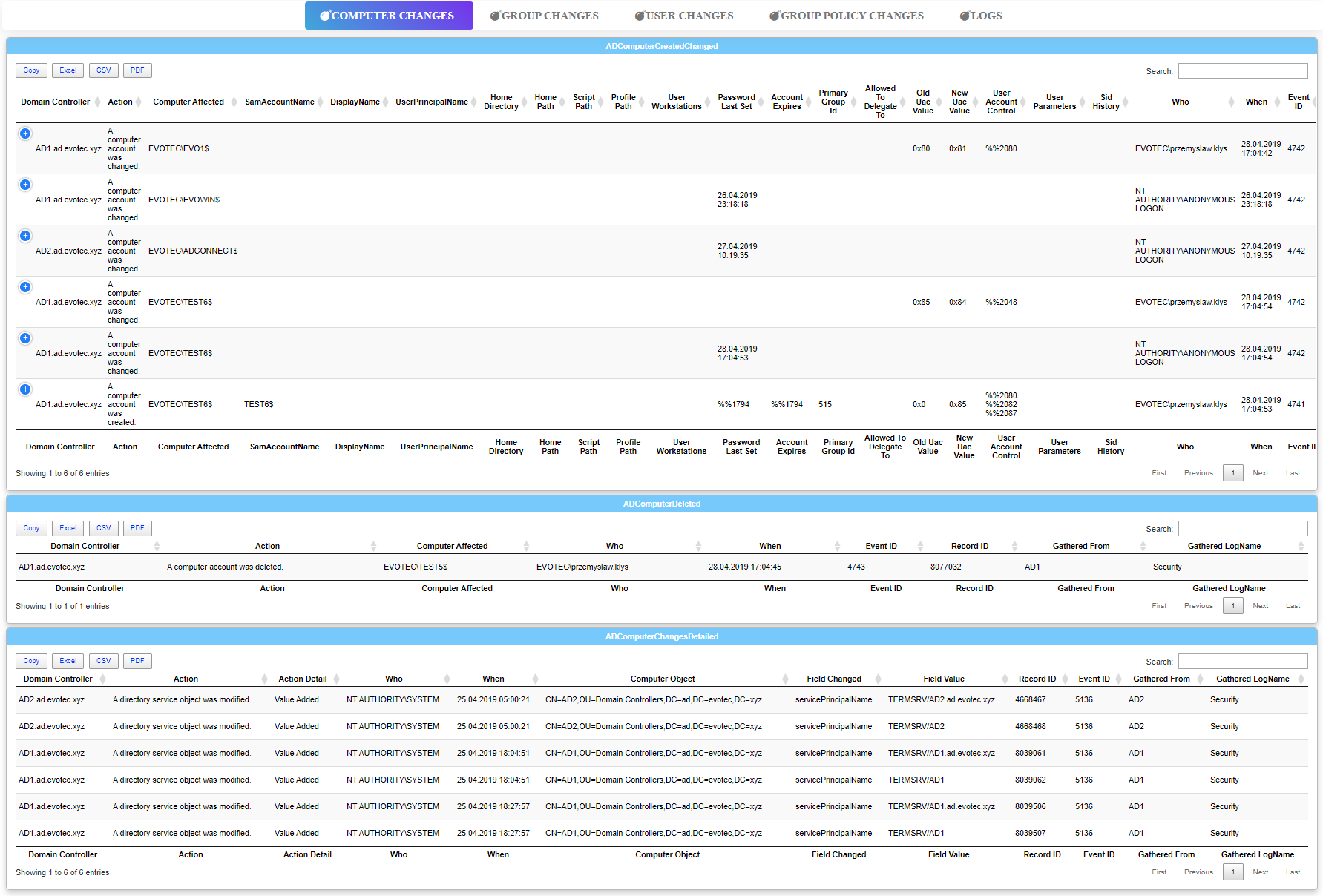
Dashboard -FilePath $PSScriptRoot\DashboardFromEvents.html -Name 'Dashimo - FindEvents' -Show {
Tab -Name 'Computer Changes' {
Section -Name 'ADComputerCreatedChanged' {
Table -DataTable $Events.ADComputerCreatedChanged
}
Section -Name 'ADComputerDeleted' {
Table -DataTable $Events.ADComputerDeleted
}
Section -Name 'ADComputerChangesDetailed' {
Table -DataTable $Events.ADComputerChangesDetailed
}
}
Tab -Name 'Group Changes' {
Section -Name 'ADGroupCreateDelete' {
Table -DataTable $Events.ADGroupCreateDelete
}
Section -Name 'ADGroupMembershipChanges' {
Table -DataTable $Events.ADGroupMembershipChanges
}
Section -Name 'ADGroupEnumeration' {
Table -DataTable $Events.ADGroupEnumeration
}
Section -Name 'ADGroupChanges' {
Table -DataTable $Events.ADGroupChanges
}
Section -Name 'ADGroupChangesDetailed' {
Table -DataTable $Events.ADGroupChangesDetailed
}
}
Tab -Name 'User Changes' {
Section -Name 'ADUserChanges' {
Table -DataTable $Events.ADUserChanges
}
Section -Name 'ADUserChangesDetailed' {
Table -DataTable $Events.ADUserChangesDetailed
}
Section -Name 'ADUserLockouts' {
Table -DataTable $Events.ADUserLockouts
}
Section -Name 'ADUserStatus' {
Table -DataTable $Events.ADUserStatus
}
Section -Name 'ADUserUnlocked' {
Table -DataTable $Events.ADUserUnlocked
}
}
Tab -Name 'Group Policy Changes' {
Section -Name 'ADGroupPolicyChanges' {
Table -DataTable $Events.ADGroupPolicyChanges
}
}
Tab -Name 'Logs' {
Section -Name 'ADLogsClearedOther' {
Table -DataTable $Events.ADLogsClearedOther
}
Section -Name 'ADLogsClearedSecurity' {
Table -DataTable $Events.ADLogsClearedSecurity
}
}
}
If you liked this article take a moment and review my other work in Technical HUB or see all my PowerShell based projects on GitHub. If you play with PowerShell a little bit I'm sure you will enjoy what you will find there.