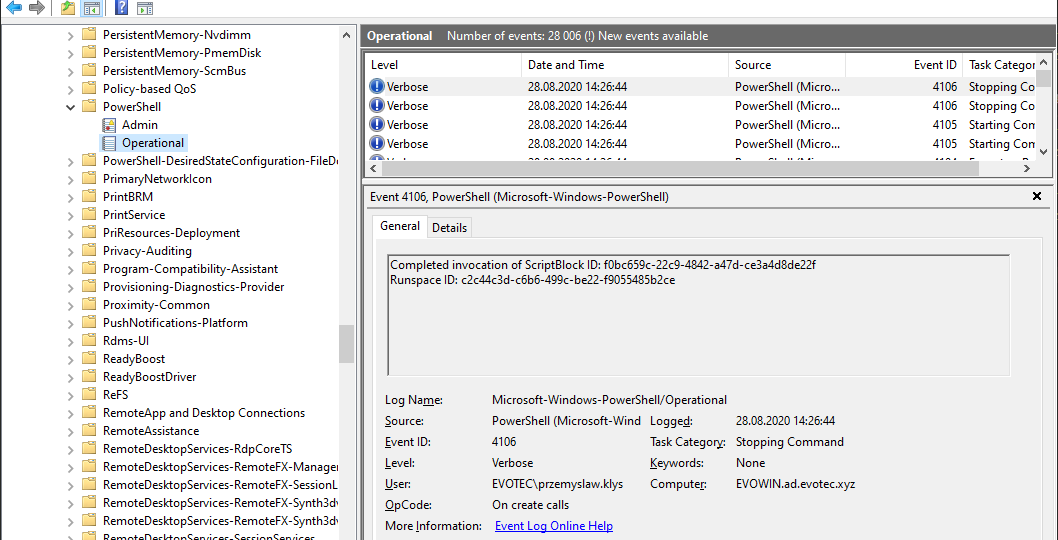
A few days ago, I was asked to take a look at PowerShell Malware. While I don’t know much about malware, my curiosity didn’t let me skip on this occasion, and I was handed over WindowsPowerShell.evtx file. Ok, that’s not what I expected! I wanted PowerShell .ps1 files that I can read and assess? Well, you play with the cards you were dealt with. What I was handed over was PowerShell Event Log. PowerShell writes whatever you execute, and it thinks it is risky, to Windows PowerShell Operation Event Log.
Przemyslaw Klys
Today, I’m introducing a new PowerShell module called Mailozaurr. It’s a module that aims to deliver functionality around Email for multiple use cases. I’ve started it since native SMTP cmdlet Send-MailMessage is obsolete, and I thought it would be good to write a replacement that adds more features over it as things around us are changing rapidly.
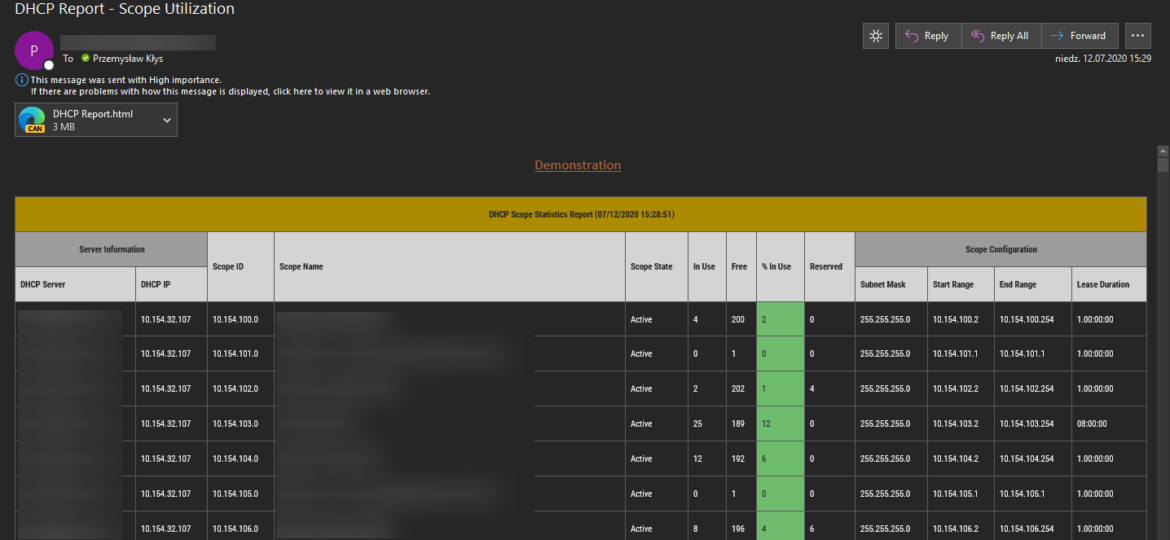
I’m pretty addicted to reading blog posts. I saw this new blog post the other day, where the author created the DHCP HTML report, and he did it by manually building headers, footers, table borders, and finally, adding some coloring to the percentage of DHCP being in use. It’s the “standard” approach to build HTML in PowerShell, and I’ve seen a similar path before, but that got me thinking how much time it would take for me to replicate the very same functionality using PSWriteHTML module.
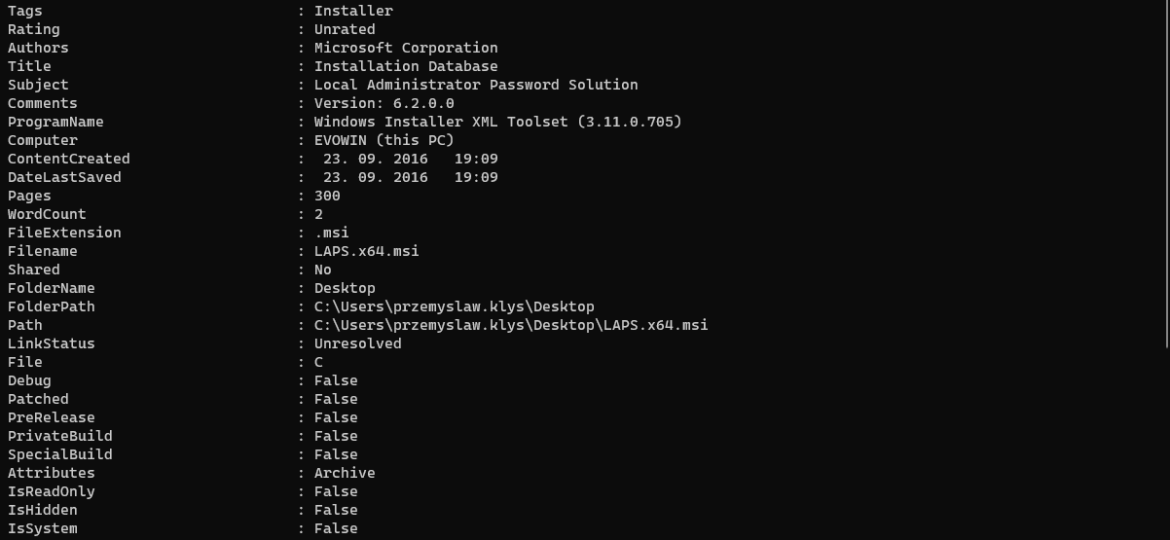
I’m working on a new feature for one of my modules that requires me to know what kind of files I am working with. It’s quite easy in PowerShell, and without a lot of code, you can reasonably quickly get necessary information about data stored on your desktop or anywhere else for that matter.
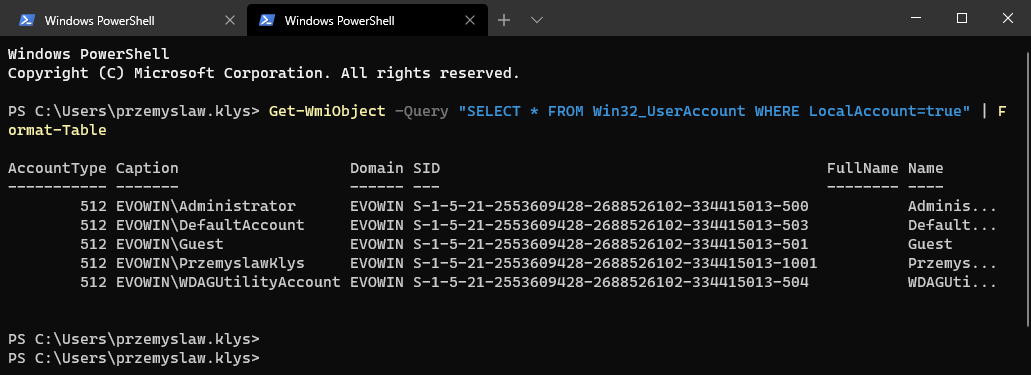
Some months ago, I created PowerShell Script to create local administrative users on workstations – Create a local user or administrator account in Windows using PowerShell. It’s a bit overcomplicated, but the goal was it should work for Windows 7 and up, and that means supporting PowerShell 2.0. As part of that exercise, I’ve been using Win32_UserAccount WMI based query to find local users and manage them to an extent. While Get-LocalUser exists, it’s not suitable for the PowerShell 2.0 scenario. I also use the same query in GPO for WMI filtering. You can say it’s been a good friend of mine.
Now that Pester V5 is out, I decided that I need to make sure that my Pester tests for all my modules keep on running correctly. Some substantial changes in Pester add new features, changing some things, but that also means all the tests that you have defined most likely will need a small push to get it up and running again on Pester V5. Starting this blog post, I wanted to mention that I am by no means an expert on Pester, but I do use it for some time now for most of my projects. I am using basic functionality, but even that basic functionality stops working once you upgrade from PesterV4 to PesterV5, so I thought I would save you some time and give you a small overview of how you can quickly fix it. It works for me, but you may have to find your way to fix things.
In the last weeks, I’m working on a PowerShell module that the main goal is to work on gathering and fixing GPOs. I’ve been testing my module a lot of times on my test environment, and it worked fine till the moment I run it on production, and it started to fail pretty quickly. The difference between my environment and production is 25 GPOs vs. 5000 GPOs. The error I was getting:
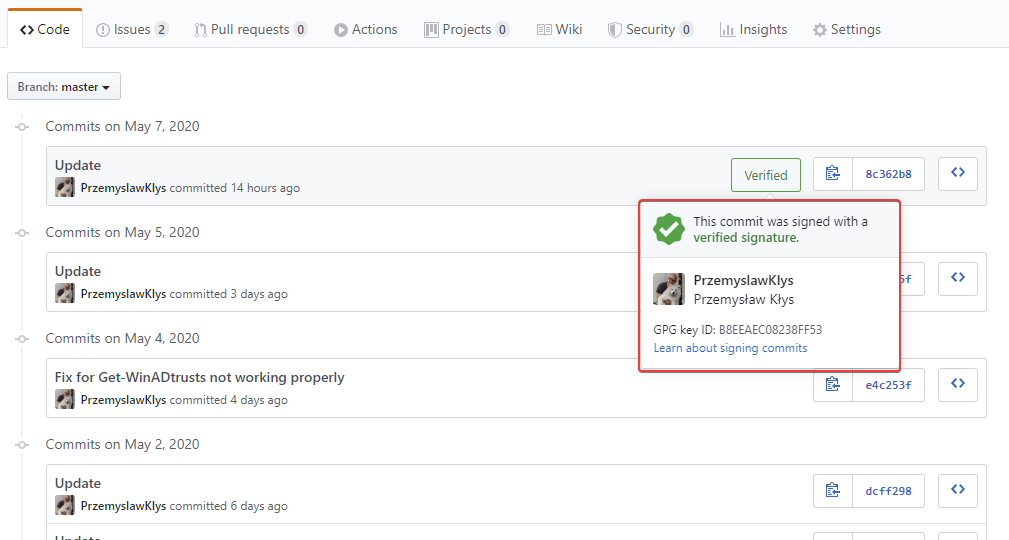
A bit over two years ago, I started posting my PowerShell code as modules on GitHub. Initially, I planned to have them hosted on my website, but few people asked to post it there, and they were right. It would be fairly hard for me to keep my code up to date on my website and, at the same time, let people submit bug reports or help with some PR. It was the right decision! Now that I’ve worked for over two years on GitHub as a daily driver, I wanted to get a new green badge that’s shown on GitHub when you edit some code. I don’t know if you ever noticed, but if you write any code, text file directly via the GitHub.com webpage, your commits always have Verified badge next to them.
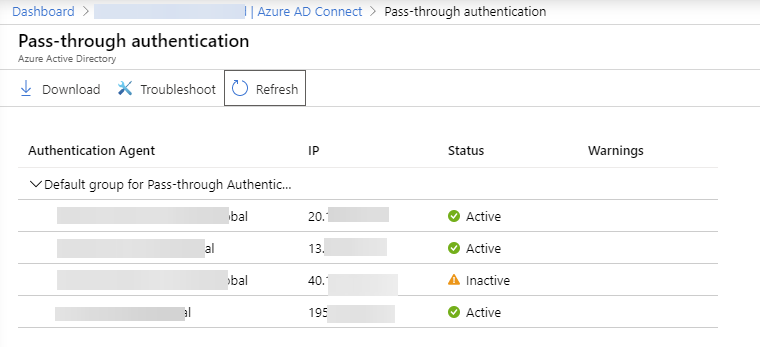
Recently I was switching Office 365 tenant from ADFS to Azure AD Pass-through authentication (PTA). It all went smoothly with one exception. After removing one of the Azure AD Connect servers and all applications from its Azure AD Connect interface still is showing said agent, just inactive.
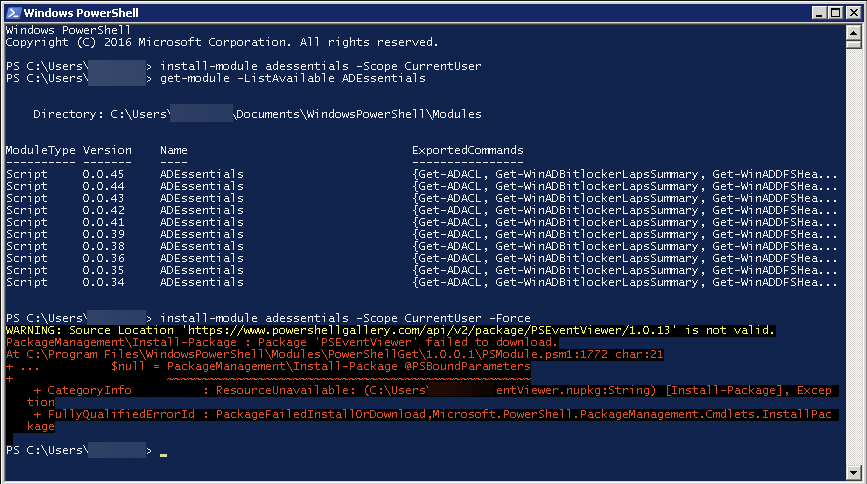
A few days ago, I tried to use Install-Module on the old Windows 2008R2 system that I use for specific tasks.