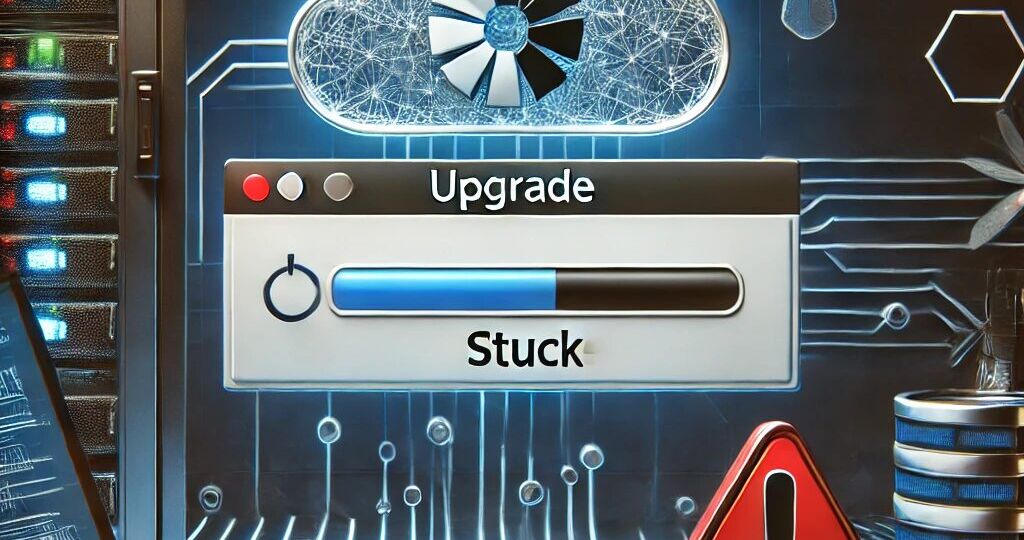
Today, I made the decision to upgrade my test environment and update the version of Azure AD Connect to the latest one. The process is usually simple: download a new MSI, run it, click next a few times, enter the credentials for your Global Admin, and you’re finished. However, this time, I encountered an error.
azure ad
Active Directory (AD) is crucial in managing identities and resources within an organization. Ensuring its health is pivotal for the seamless operation of various services. Today, I decided to look at Microsoft Entra Connect Health (Azure AD Connect Health) service, which allows monitoring Azure AD Connect, ADFS, and Active Directory. This means that under a single umbrella, you can have an overview of three services health. But is it worth it?
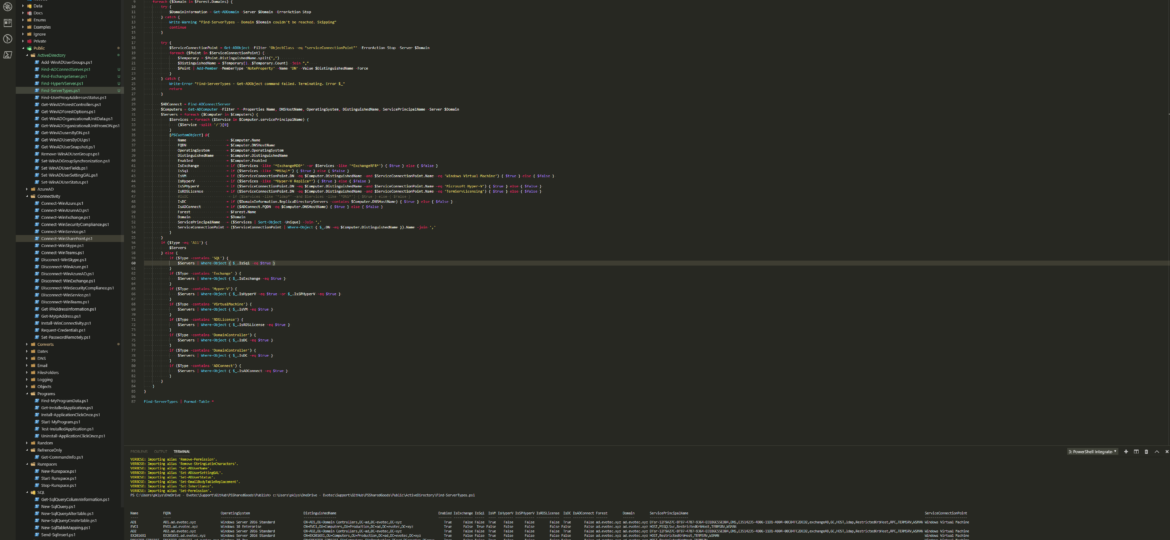
I was scrolling X (aka Twitter) today and saw this blog post, “PowerShell: Report On-Premises Active Directory Accounts that are Synchronized with Azure AD Connect” by Kevin Trent. I like reading blog posts as I tend to learn some new things and see how people tend to solve their problems.
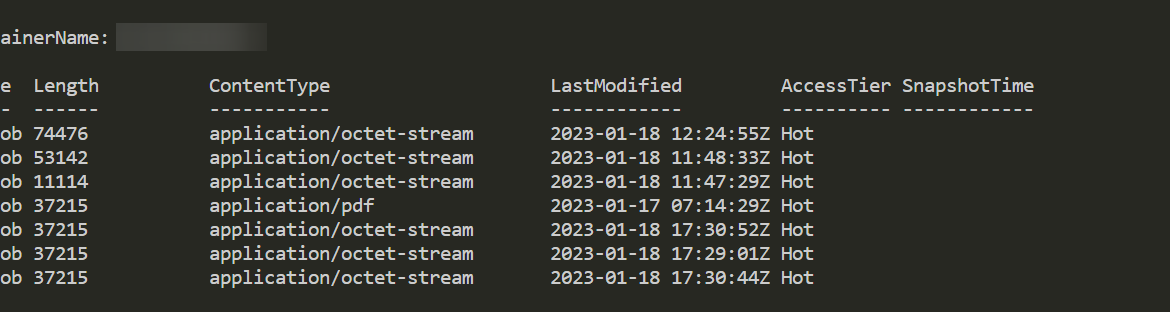
They say there is a first time for everything. For me, it’s how to download and upload files to Azure Blog Storage using Connection String. Recently I was given Connection String, Container name and had to download some files from Azur Blog Storage. After some research and trying Connect-AzAccount, I found that the proper way to go is thru New-AzStorageContext.
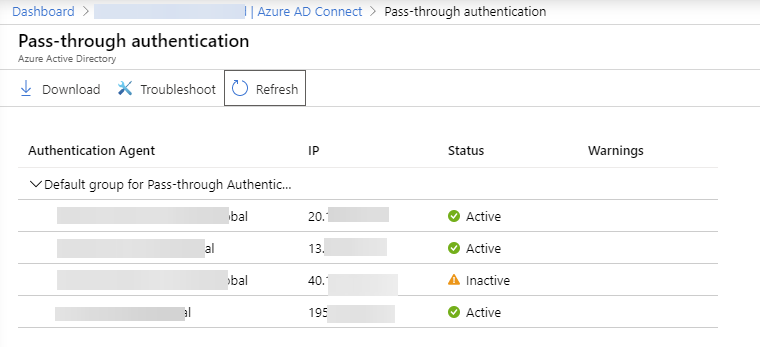
Recently I was switching Office 365 tenant from ADFS to Azure AD Pass-through authentication (PTA). It all went smoothly with one exception. After removing one of the Azure AD Connect servers and all applications from its Azure AD Connect interface still is showing said agent, just inactive.
Office 365 has a lot of options and applications to choose from. Enabling one E1, E3, or any other license gives the user a lot of features, including Exchange, SharePoint, and Teams. But what if you want to make sure that the user can access only Microsoft Teams? By default, you can do it manually during the assignment of the license. Simply choose only Apps you want to assign to a user.
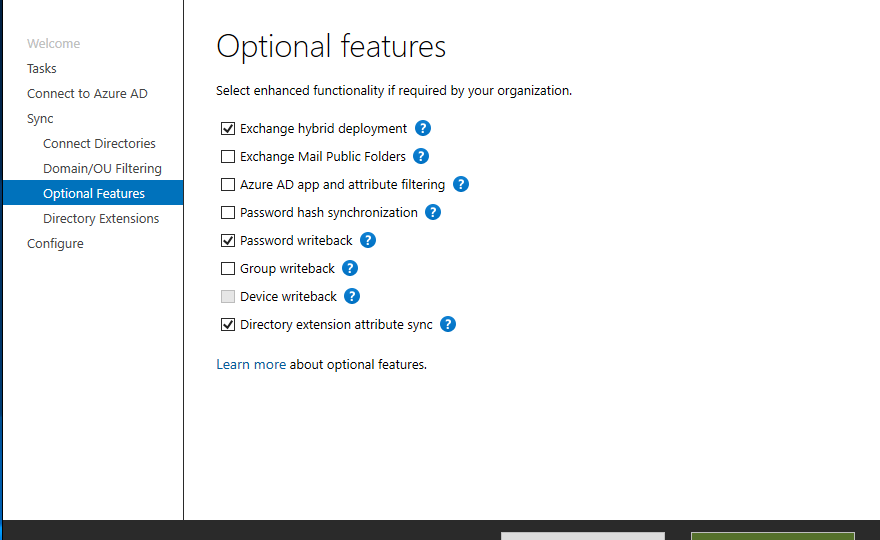
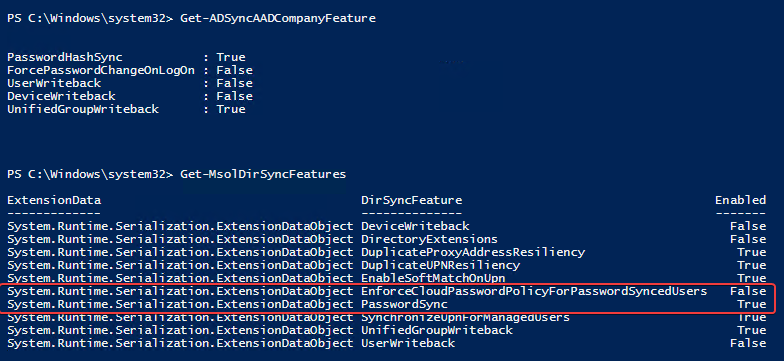
Azure AD Connect allows three ways to make sure the user password is the same in Active Directory and Office 365. Those are Password Hash Sync, Pass-Thru Authentication, and ADFS. While my preferred option to go with would be Pass-Thru Authentication, only Password Hash Synchronization is the easiest and least resource-intensive. It synchronizes user password to Office 365, and even if your Active Directory is down, you can still log in to Office 365. It’s perfect for small and even more significant companies that don’t have resources or can’t guarantee that their infrastructure will stay 100% time online so users can authenticate based on their Active Directory.
Working as a freelancer is a great thing if you can handle it. Each day, each week something new happens and a new problem shows up on my doorstep. It also means it’s almost never boring at your job and you get to play with new stuff. But there’s one drawback to this. You’re often thrown at the problem, told to fix it but often that’s about as much information as you get. It wasn’t very different today. I was told to switch Office 365 from ADFS to Password Synchronization. While reasons for this are not really important, the important question here is what is the name of AD Connect server that’s responsible for this configuration?
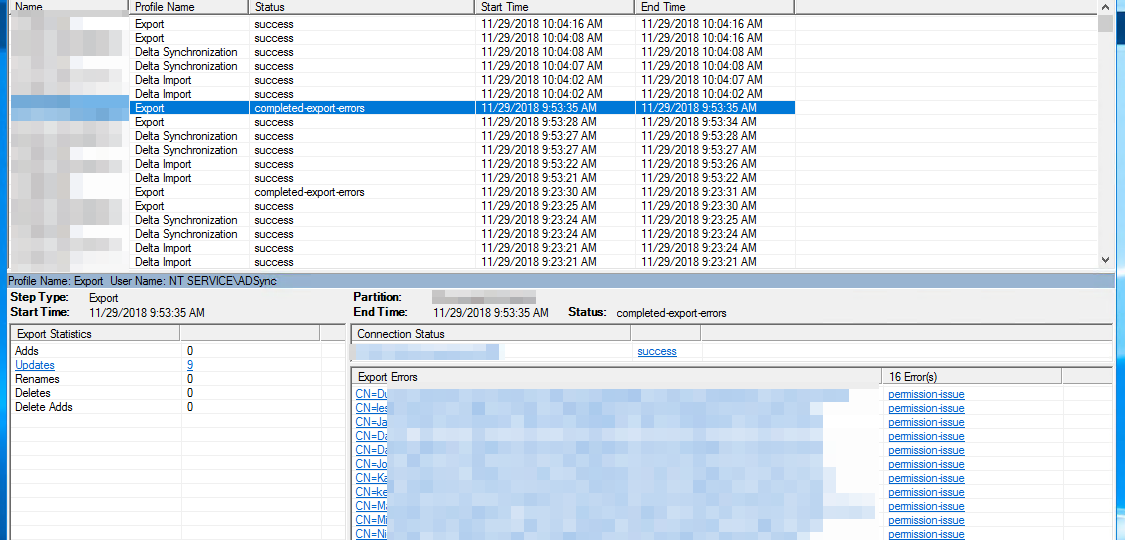
During synchronization of Active Directory with Office 365 via Azure AD Connect I was greeted with a list of accounts that have permission-issue. Error message by itself gives you a slight hint, but it doesn’t tell you exactly where to look.